Food Delivery Leak Unmasks Russian Security Agents
Russian tech giant Yandex has blamed one of its employees for the hacking and subsequent leak of data from Yandex Food, a popular food delivery service in Russia.
Among the many users affected are serving agents of Russia’s security services and military, who in several cases even ordered food to their places of work using their official email addresses.
This leak includes user emails, a large number of phone numbers, addresses, and orders made on the platform. Russia’s state media watchdog Roskomnadzor has strongly attempted to block its proliferation.
Some investigators have already uncovered leads for investigations into corruption from this data leak, namely the 170 million ruble (~$2 million USD) apartment of Russian president Vladimir Putin’s reported “secret daughter”.
Благодаря слитой базе «Яндекса» нашлась ещё одна квартира экс-любовницы Путина Светланы Кривоногих. Именно туда их дочь Луиза Розова заказывала еду. Квартира 400 м², стоит примерно 170 млн рублей!https://t.co/z3uGKOdQhc pic.twitter.com/tOGXOsFmRY
— Соболь Любовь (@SobolLubov) March 23, 2022
Bellingcat has analysed the data to verify its authenticity and uncover new investigative leads. By cross-referencing data points within this leak to independent sources including social media profiles and other leaked databases, we can confirm that it is indeed authentic. However, as with most data leaks, the vast majority of this information does not have legitimate research purposes, therefore we are not linking to the data itself. Personal details have been obscured in screenshots throughout this article.
We have only used this leak to explore further information about the subjects of previous investigations – many of whom are members of Russia’s security services and military.
What’s in the leak?
The main part of the data leak includes order information, along with some personal information collected from the user. These include their Yandex.Food ID, address, contact details, delivery instructions, billing information and metadata.
One address Bellingcat searched for is Dorozhnaya Street 56 in Moscow. This facility is linked to the Russian National Guard (Rosgvardia), which has been active in the invasion of Ukraine.
First, here’s an example of how personal details of users who ordered food are displayed in the leak.
The first name is a required field, but full name is often left blank. Below, a fictional Andrey Andreyev has placed their order. The email field is also optional, though the phone number is required. In some cases, user data with phone number, name, and email will be included even if an order has not been placed — likely from when a user has registered but not placed an order on the app.

Data with generic personal information, for illustrative purposes
Also included is the delivery address — not to be confused with the user’s home address, which is not included in this data — with accompanying delivery instructions. These delivery instructions, as detailed later in this article, are some of the most fascinating data points of this leak.
In the case below, showing address and delivery instruction data that reflects an actual Yandex.Food order, the customer specified that the order is being sent to military unit 3792, and that they should call the listed number when they arrive to pick it up at the front gate. This military unit number corresponds to the 681th Special Motorised Regiment of Rosgvardia.
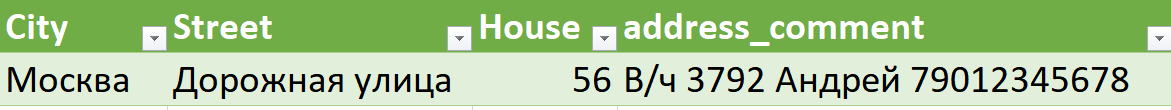
Entry from a order sent to a Rosgvardia base, with depersonalised phone number and name for illustrative purposes
The final fields are the user’s latitude and longitude at time of order, the amount charged for the order (738 rubles, which equates to roughly US $8.76), the operating system or browser used, the time of order, and lastly any user comments regarding a door code.
For researchers, the coordinates are probably the only useful field here, as the coordinates usually match the address for delivery. In this case, they coincide with the Dorozhnaya 56 address in Moscow.

Entry from a order sent to a Rosgvardia base, with depersonalised operation system data
The vast majority of this data concerns ordinary Russian citizens whose ordering habits are not hugely useful for investigative research. However, specific targeting of addresses, phone numbers, names, and notes in delivery instructions pointed our researchers to some interesting leads.
GRU to MFA?
We searched the phone numbers in the leak for a range of individuals linked to the GRU, Russia’s foreign military intelligence service, whom we have discovered over the past few years.
One of these numbers is for a man named Yevgeny who was linked to the GRU Academy and was a contact of high-ranking GRU officer Andrei Ilchenko. After searching for his phone number, we found an order he placed to 1st Neopalimovsky Lane 12 in Moscow. This address is publicly listed as being owned by the Ministry of Foreign Affairs’ Consular Service. Further research into this individual through leaked Moscow oblast vehicle registration information revealed a license plate to a luxury car, which was photographed in Kyiv in 2019.
It’s unclear if Yevgeny is still linked to the GRU or if he has a new job at the MFA, but thanks to the information revealed in his food delivery order it became possible to dig further into his recent activities.
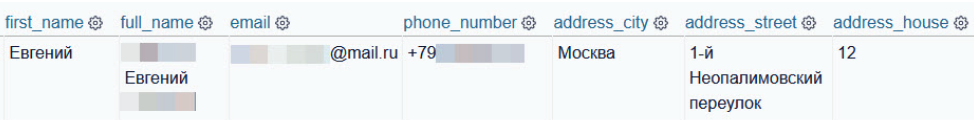
User information pointing to a Ministry of Foreign Affairs building
FSB interlocutor identified
During our investigation into the poisoning of Alexey Navalny by a team of FSB officers, we analysed numerous calls made by phone numbers linked to those carrying out and planning the operation.
One number which surfaced quite often was to a research institute in Dubna, a northern Moscow suburb. We were unable to identify the owner of this phone number until searching for it within the Yandex.Food leak, which revealed the name of this person, who frequently spoke with the FSB officers planning Navalny’s poisoning. It is unclear exactly what role this person had with the organization and execution of Navalny’s poisoning, but he was on the phone with one of the FSB team members on the night of the poisoning and the following morning when Navalny was rerouted to Omsk.
What’s more, he used his work email address when registering for the service, making it clear that this is the same person and not just a recycled phone number with a new owner.
Military and security service identities
Perhaps the most obvious use for this database (at least for Bellingcat) is to cross-reference the personal details of users with the functions of the facilities at addresses used for orders — in other words, to find spies and soldiers.
Let’s start with something simple: the address of the GRU headquarters in Moscow, at Khoroshovskoye Shosse 76.
Searching for this address brings up four results (two each for two different users named Danila). These are only a few results for what is a large facility, suggesting either restraint on the part of GRU staff, or a number of walkable eating options nearby.
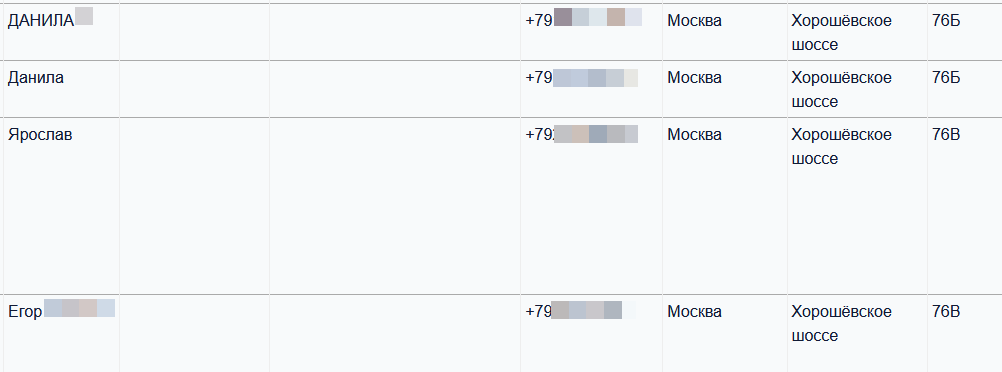
Four orders sent to the GRU headquarters in northwestern Moscow
We cannot ascribe the same restraint or choice of food options to the FSB.
Searching for the FSB’s Special Operation Centre in the Moscow suburb of Balashikha brings up 20 results. One reason for this could be the more remote location of this facility, compared to the more centrally located GRU headquarters. These results often contain detailed instructions on how the delivery driver should get the food to the user; one user wrote: “Go up to the three boom barriers near the blue booth and call. After the stop for bus 110 up to the end”.
Another user wrote: “Closed territory. Go up to the checkpoint. Call [number] ten minutes before you arrive!” This number is likely a second number linked to the same user.
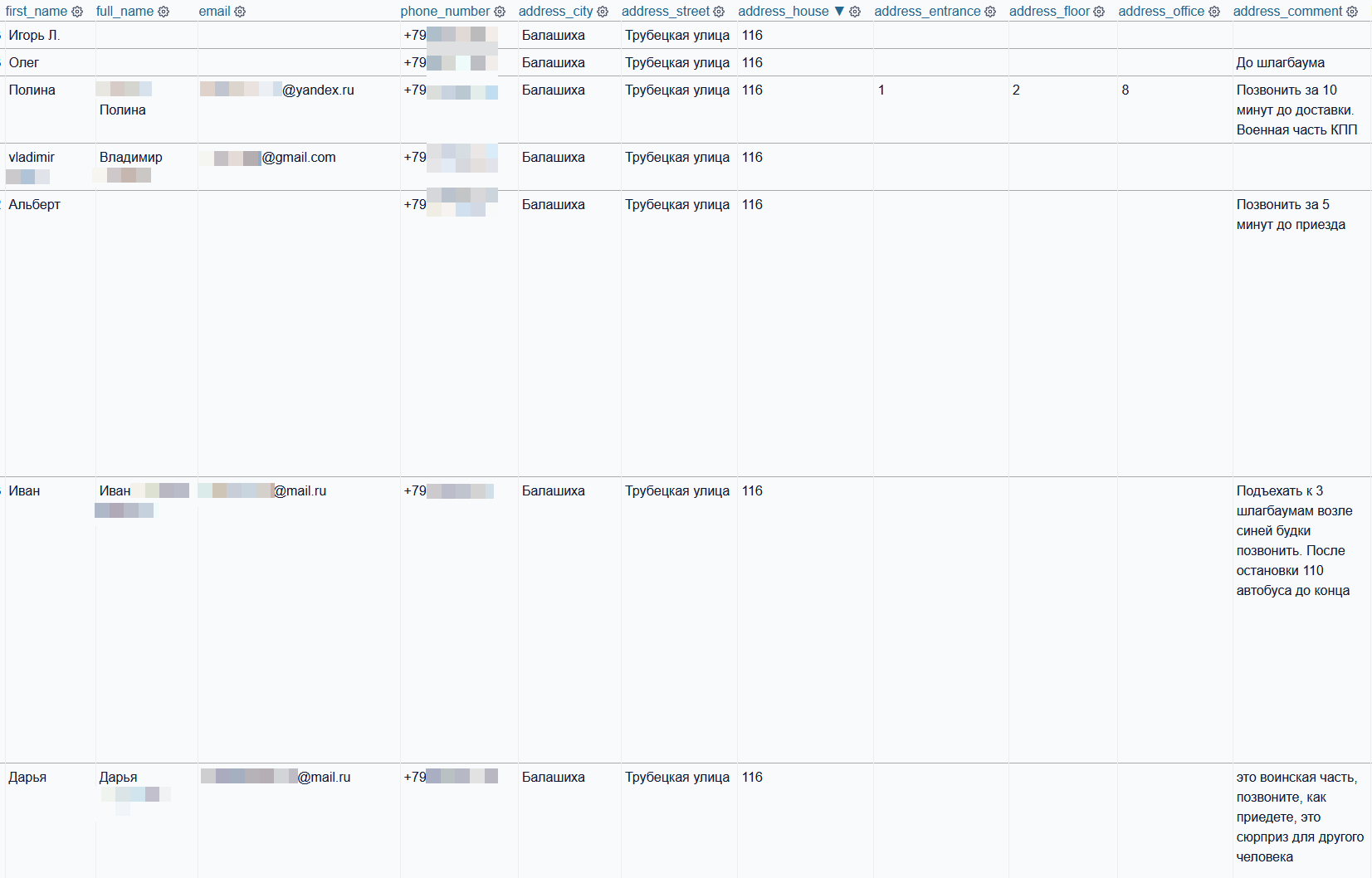
A selection of orders sent to the FSB’s Special Operations Centre in a Moscow suburb
Fishing for interesting addresses
Along with searching for known addresses which are already of interest — military bases, FSB and GRU offices and so on — you can also search among the delivery instructions to fish for new places that may be worth digging into. For example, by searching for войсковая часть (military unit) in the delivery instructions field, a few dozen results appeared which warned that the delivery location is a military base and requires drop-off at a checkpoint at the entrance. In some cases the user notes the specific military unit number in the instructions.

Delivery instructions to facilities linked to military units in Kazan and Yekaterinburg
Leaks continue unabated
This leak marks yet another entry into a long list of massive data breaches for Russian citizens, some of the largest of which include vehicle registration data, social media platform (VK) user information, and comprehensive air travel records.
Steady streams of data flow out of Russia for a number of reasons, but the most obvious include petty corruption, pervasive human error and the state’s own comprehensive surveillance laws being turned against them.
Following the “Yarovaya Laws” being adopted in 2016, Russian telecom operators were required to maintain customer data. This data was intended just for the security services to use, but is also often illicitly sold to online buyers. Thus, a law meant to strengthen the FSB and other security services has been used against them when Bellingcat and other investigative outlets acquire the retained telecom data of FSB officers to reveal wrongdoing.
With increased cyberattacks from Ukrainian and pro-Ukrainian hacker organisations, we should expect to see more government and customer databases leaked, some of which may be of use in investigating matters in the public interest.
Additional research by Michael Sheldon, Logan Williams and Bellingcat’s Investigative Tech Team
Correction: This story initially stated that passwords were part of the Yandex Food leaks when they were not. The text has been updated to reflect this.


