Anatomy of Three Leaked US Intelligence Documents
Among the documents leaked on the social messaging platform Discord in February 2023 were three purported damage assessments from recent strikes by the Ukrainian Armed Forces on Russian targets behind the front lines.
These documents are among hundreds that were allegedly posted onto Discord channels throughout 2022 and 2023 by accused leaker Jack Teixeira, a U.S. National Air Guardsman who was arrested on April 13.
While the US government has not officially confirmed the authenticity of the documents, the charges levelled against Teixeira accuse him of leaking classified military documents.
While it has been widely reported that the US has shared intelligence and targeting data with Ukraine following Russia’s full-scale invasion, it is unclear if these assessments are occasions where this was the case. It is also possible that the documents detail analysis or intelligence gathering on Ukrainian operations which the US became aware of only after they took place.
Still, the documents are revealing given they highlight US intelligence gathering around the invasion as well as some of the satellite and analytical resources at its disposal.
Neither the US Department of Defense nor Ukraine’s Ministry of Defence had responded to Bellingcat’s requests for comment by the time of publication.
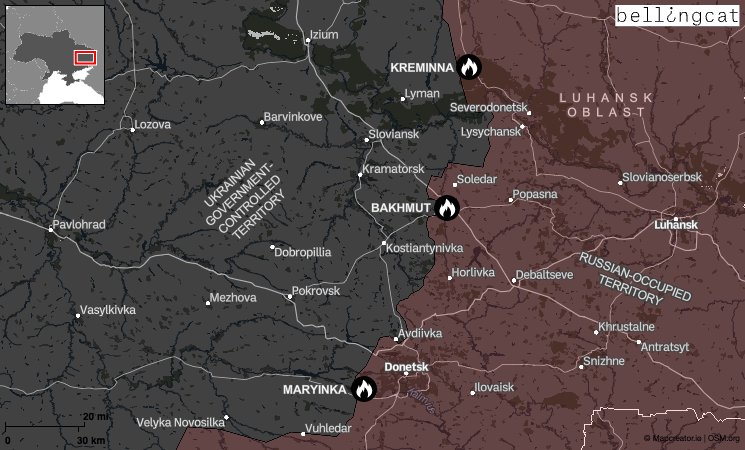
A Building in Maryinka
One of these documents, titled “BDA from Recent Strike? 15Feb23 KP0041 – Damage GBU BBCARD”, shows two aerial images depicting damage to a handful of buildings near Maryinka, a largely destroyed frontline town in the Donetsk Region of eastern Ukraine, along with a “pre-strike” image captured on February 10. BDA means Battle or Bomb Damage Assessment, while GBU means Guided Bomb Unit.
This interactive image of this BDA shows key terms which are shared across many of the documents. Hover over or tap the highlighted sections to read the explanations.

The first thing to note that this BDA includes a significant error. The coordinates indicating a target at the grid point 47.834949, 37.655150 refer not to the building seen in the satellite imagery, but instead to a petrol station in the occupied town of Olenivka, south of the city of Donetsk. This petrol station actually lies nearly 15 kilometres away from the target. Bellingcat could find no evidence in commercial satellite imagery that the petrol station in Olenivka also sustained damage around the time of this BDA.
Bellingcat has been able to geolocate (47.9450674,37.5817775) the building seen in the satellite imagery on which this BDA was based. According to YouControl, a Ukrainian online company verification service, it was the premises of a car transportation firm. It appears to have since been repurposed by Russian forces for military use. In November 2014 the Warfare Log, a now defunct blog covering military developments in eastern Ukraine, claimed that two Tyulpan systems (self-propelled heavy mortars of Soviet design) had been destroyed at this location, indicated by the same business code number seen on the YouControl webpage. As the Warfare Log did not share any visual evidence for this claim, Bellingcat cannot independently verify the incident.
However, in July 2015 the pro-Russian Novorossiya Support Foundation shared a video showing Russian tanks and Russian-led forces present at the compound. Twitter user and ‘OSINT enthusiast’ @5urpher was the first to correctly geolocate this video; both target buildings were visible in the background.
The Google MyMap which included the geolocation and was shared by @5urpher has since been deleted. Nevertheless, Bellingcat had been able to independently confirm the accuracy of the geolocation beforehand.

Another video from this location was posted to Twitter on 3 February 2023; it was correctly geolocated by Twitter user @neonhandrail, a volunteer at GeoConfirmed, a group of digital researchers geolocating footage from Ukraine. The footage showed BM-21 ‘Grad’ multiple launch rocket systems (MLRS) operating within the compound and taking artillery fire.
As the date on this BDA indicates, the Ukrainian strike against the same location came just two weeks later. While the BM-21s can be seen in use at this location, it is unclear if they were stored here permanently. Tracks visible in the footage suggest it’s possible they could have recently been moved there or that they regularly drove in and out.
Ukrainian artillery hit the Russian MLRS BM-21 Grad. #Donetsk , Donetsk Oblast
— Neonhandrail (@neonhandrail) February 4, 2023
@GeoConfirmed 47.943884, 37.583381https://t.co/Vt8tFV9YGV pic.twitter.com/4ABdy1Tffr
According to the same document, the strike was targeting Russia’s 8th Guards Combined Arms Army which according to the US Congress reportedly commands some units from the so-called Donetsk People’s Republic’s militia. The BDA noted that three precision munitions were used on two target buildings, of which only one munition hit its target.
The post-strike imagery consists of what appear to be two drone photographs, given the low altitude, angled vantage point and high level of detail provided. The source for these is listed as “OSINT” in the document; however, Bellingcat was unable to find the original source for these images.
The pre-strike satellite imagery, seen in the small box at the top-right of the document, has a catalogue identification number of 10FEB232211D9084000E000; however, it is unclear to which catalogue this refers. The commercial satellite company Maxar also uses 16-character catalogue numbers, but the image taken most closely to this one – on 8 February, two days prior to the image in the document – is labelled as 1040540029FB9D00. This catalogue identification differs greatly in serialisation (starting with 104- rather than 221-) and formatting (the letters being in different locations in the ID) from that in the leaked document. It is possible that this satellite imagery comes either from a service contracted by the US government or US government-owned and operated satellites, such as Keyhole.
The BDA was written by “SAG-U”. According to a press release on the US Department of Defense website, this refers to the department's Security Assistance Group - Ukraine, based in Wiesbaden, Germany. The description of the “US-Produced / Mensurated Target” is especially interesting, and not entirely clear. While it is possible that the United States initially discovered this target, relayed targeting data to the Ukrainians as has reportedly happened before, and then assessed the strike, this note may also refer strictly to the assessment itself — it was produced and measured (mensurated) by the SAG-U group, who “confirmed severe damage” in their assessment.
An inspection of Planet's SkySat imagery of the site reflects the assessment from the leaked document. The comparison slider below shows the site on February 13 (before the attack) and March 26 (after).
The building on the eastern side of the compound appeared to have been destroyed, with debris visibly spilling into the adjacent field. No structural damage to the other, smaller, target building as specified in the BDA was visible.
A Bridge in Kreminna
A second BDA in the trove of leaked documents shows the aftermath of a strike on a bridge near Kreminna, an occupied city in Ukraine’s Luhansk region which has been the site of fierce fighting.

The BDA from a strike on February 19 showed a bridge on the Krasna River north of Kreminna. The satellite imagery is explicitly noted to be from DigitalGlobe, referring to a service provided by the commercial satellite company Maxar.
It is not known why the title of the document ends in a question mark, nor if elements of the document are supposed to be speculative. There is much less information in the header than in the previous BDA; the text at the bottom of the document is also shorter, with a white space beneath where the description ends.
This BDA stated that one out of two precision munitions fired at the bridge struck it, causing severe damage.
The comparison slider below shows planet SkySat imagery of the area after the attack on February 19 and then on March 6.
Judging by the February 19 satellite imagery (with snow on the ground), the destroyed bridge had seen heavy use by Russian forces in the area as they fought for control of the forested areas outside the city. Wide and clear tracks can be seen leading from the bridge before branching out towards Russian positions. Importantly, a series of tracks can be seen leading to the riverbank about 100 metres downstream from the damaged bridge, suggesting the construction of a replacement bridge.
By March 6, tracks can be seen leading to the new bridge on both banks of the river, suggesting that it is now in regular use.
Both bridges are indicated with red boxes in the satellite imagery. They remain a major crossing point for Russian forces near Kreminna.
An inspection of Planet's SkySat imagery of the site reflects the assessment from the leaked document. The comparison slider below shows the site on February 13 (before the attack) and March 26 (after).
A Mineshaft in Bakhmut
Another BDA showed before and after imagery of a strike in a forest near Bakhmut, which it described as an “assembly area” for Russian troops. The city in Ukraine’s Donetsk Region is now surrounded on three sides by Russian forces; the grinding battle for its control has become one of the deadliest since Russia’s full-scale invasion.
Bellingcat was able to geolocate this structure, confirming the accuracy of the coordinates given in the BDA.

The precise source of this imagery is unknown. However, the document includes a few clues. The code given in the 'Pre-Strike Image ID' field in the top left has the same number of digits as in the BDA about Maryinka, indicating that the two incidents may have used the same image provider. However, unlike the Maryinka BDA, in this document the digits end in an .ntf file extension. According to LeadTools, a digital toolkit developer, this is a raster file extension also known as NITF or National Imagery Transmission Format and is used by the US Department of Defense.
Whatever its origin, the low quality of the imagery in the BDA makes it difficult to make out distinct features. However, SkySat satellite imagery from Planet Labs showed a structure at that location which had been targeted with artillery, seemingly multiple times. According to Wikimapia, the targeted area was an entrance to a gypsum mine shaft.

Overlaying the same SkySat imagery from February 20 onto the BDA provides a clearer view of the location before the attack. The distinctive features noticed earlier turn out to be roads.

Comparing the satellite imagery with the rough terrain features in the BDA post-strike imagery from March 6, it appeared that a structure (marked with a red rectangle) at the end of the road leading into the mine shaft was targeted.

This BDA stated that severe damage to the structure was possible, due to its identifying features no longer being visible in post-strike imagery. This may, however, have been due to the low quality of the imagery, as the structure did not appear to have taken additional damage in SkySat imagery from March 6.
Two craters immediately adjacent to the structure were visible, but it is unclear when exactly they may have been created.
This BDA states that the assessment of the imagery was conducted by the “176 IS”, which refers to the 176th Intelligence Squadron. This unit based in Fargo, North Dakota, is part of the Air National Guard – like Jack Teixeira’s intelligence wing in Cape Cod, Massachusetts.
Bellingcat is a non-profit and the ability to carry out our work is dependent on the kind support of individual donors. If you would like to support our work, you can do so here. You can also subscribe to our Patreon channel here. Subscribe to our Newsletter and follow us on Twitter here and Mastodon here.






