Attack on Ukrainian Government Websites Linked to GRU Hackers
- On 23 February, on Russia’s military holiday and two days after Russian president Vladimir Putin recognised the independence of the self-proclaimed DNR and LNR, most key Ukrainian government institutions had their websites attacked in a presumed DDoS campaign. As of 16:30 Kyiv time, the websites of the Ukrainian parliament, Ministry of Foreign Affairs, and Council of Ministers, (including all individual ministerial sites), and the Security Service of Ukraine, were all unreachable (the website of the Council of Ministers was brought back online at approximately 17:10 local time; most other sites came online within two hours of the attack)
- One website that was not affected by the attack as of this time was the site of the Office of the President of Ukraine.
Independent threat researcher Snorre Fagerland, working in cooperation with Bellingcat and The Insider, has identified a web service, apparently serving as a command and control centre, which has played a role in past cyber-attacks linked to Russian state interests.
The same website also hosted cloned copies of a number of Ukrainian government websites, including the main webpage of the Office of the President. Other cloned (and modified) websites found on the service include those of the Ukrainian Ministry of Justice and of a government-run petition portal. These cloned websites were created no earlier than November 2021, around the time when Russia’s latest round of escalations against Ukraine began.
Notably the cloned version of the site of the Ukrainian president is modified to contain a clickable “Support the President” campaign that, once clicked, downloads a package of malware to the user’s computer. It is not certain what the purpose of the malware payload is at this time, nor whether the payload was operational or simply a placeholder for different malware to be deployed at a crucial moment.
Link to 2021 Cyber Attacks on Ukraine
The type of malware deployed on the cloned Ukrainian websites – which are hosted on subdomains of the generically sounding domain stun[.]site, as well as the common registrant of the IP (and domain) – show a link to previous cyber attacks on the Ukrainian government dating to April 2021, as well as on the government of Georgia. These attacks were first reported by FortiGuard Labs, and later followed-up on by Intezer. In those attacks, spear-phishing emails were sent to various security-linked organisations in Ukraine and Georgia, using social engineering baits with subjects such as: “New COVID-21 Variant” and “An Urgent Computer Update”. The goal of these attackers had seemingly been to steal sensitive documents and files as well as installing the Saint Bot downloader malware on the targets’ computers. In Ukraine, the attacks had been directed at a military veterans’ organisation and the military Anti-Terrorist Operation (ATO), responsible for countering the Russian military intervention in the Donbas.
The 2021 attacks had been attributed by the threat researcher community to a new actor, (TA) 471. Intezer, among other researchers, tentatively attributed the attack to Russia’s military intelligence (GRU) hacking department, known as APT28 or Fancy Bear. However, their conclusion was not solely based on the attacks’ telling choice of targets, which included foreign security actors deemed of interest to the Russian state. The 2021 attacks also shared a similar approach with previous confirmed APT28 campaigns. These included prior use of Covid-19 and NATO related phishing themes to target Ukraine, use of AutoIt malware scripting, use of Hex encoding, batch files, power shells and cmd scripts. Furthermore, the historical IPs behind the domain names used as command and control centres had all been attributed to Russian owners.
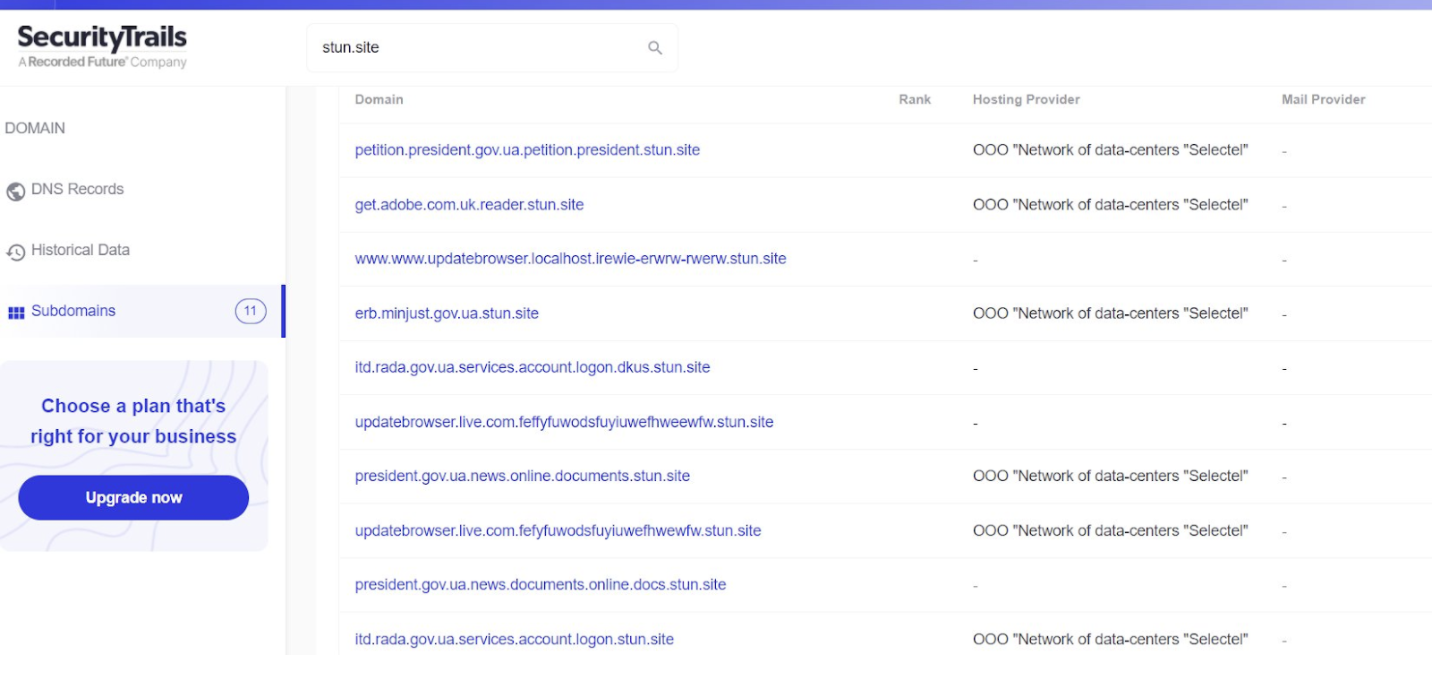
The domain where the Ukrainian cloned government sites were found appears to be linked to the same actor who was behind the 2021 attacks. According to threat researcher Snorre Fagerland, who first discovered the cluster of clone-site subdomains, this is evidenced not only by the domain name patterns (domains used in the 2021 campaign included eumr[.]site, 3236[.]site 3237[.]site 3238[.]site), but also by commonality of malware hosted on these sites and stun[.]site and similarities in domain registration information.
Attack of the Clones
Despite the similarity in hosted malware, the newly found depository (which has been taken offline after threat researchers alerted the hosting providers) was different from the websites used in the 2021 cyberattacks. This depository hosted clones of Ukrainian government websites seemingly targeted at the general public, not a specific subset of security-linked individuals likely to own non-public sensitive data of interest to a hostile state actor. Furthermore, most of the cloned sites identified contain log in pages that could be useful for stealing credentials in larger phishing campaigns. The one exception was a subdomain made to appear to be the log in portal for members of the Verkhovna Rada, Ukraine’s parliament.
Subdomains hosted on this website included a clone of the Ministry of Justice website, previously at http://erb.minjust.gov.ua.stun[.]site, and first spotted on 21 December 2021. Another was a portal for signing petitions run by the president’s office, previously at http://petition.president.gov.ua.petition.president.stun[.]site, and first seen on 27 November 2021.
“Support Mr. President”
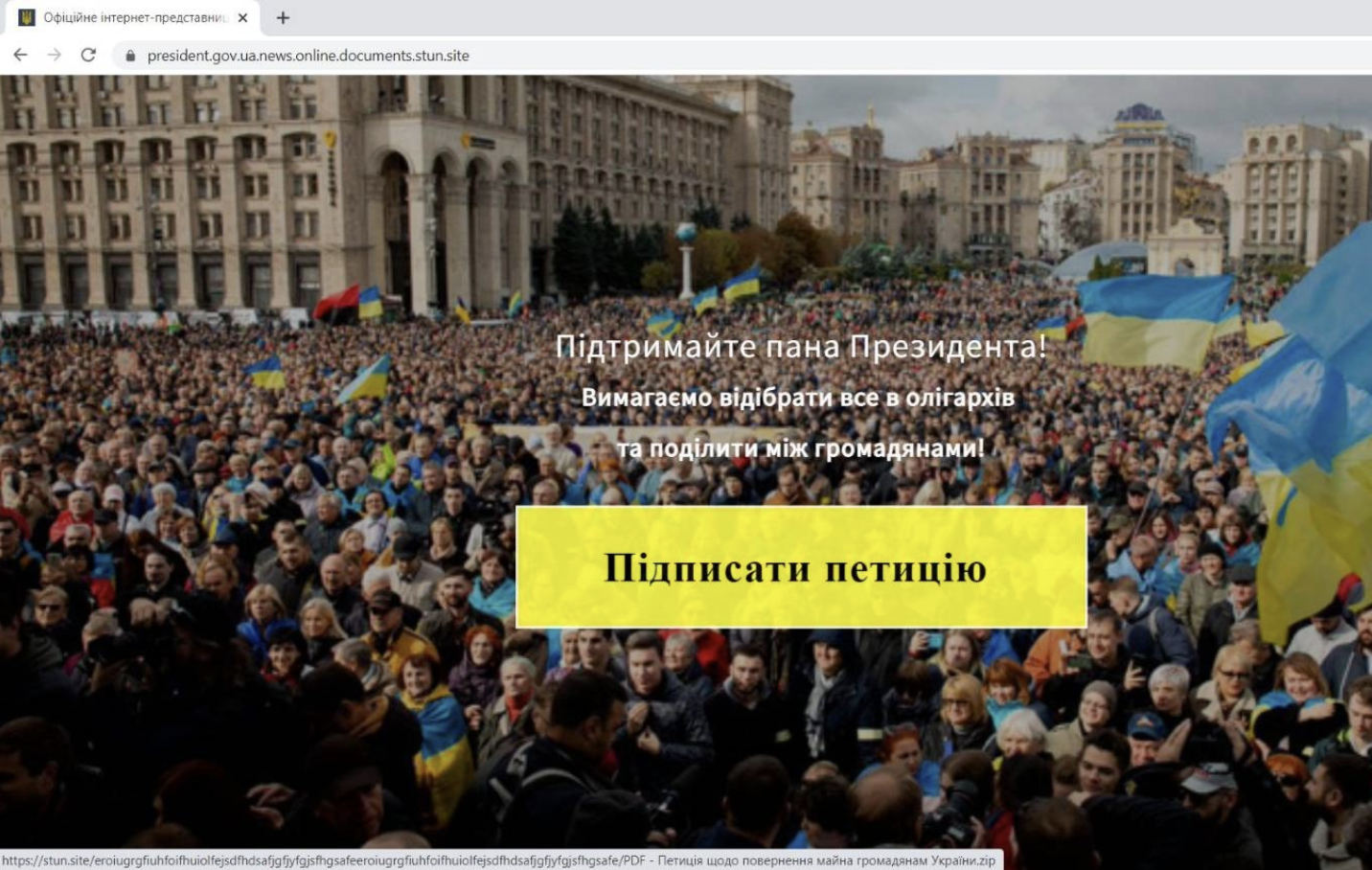
At least one of the cloned websites hosted on stun[.]site was aimed at a very broad target audience and apparently intended to infect as large a part of the population as possible. It was the official website of the Ukrainian president – or at least, it looked like it.
However, it had been modified to load a popup after a predetermined time of several seconds. The popup (shown in the screenshot below) invited visitors to “support Mr. President” to confiscate the property of all oligarchs and “share it among all citizens”. A large yellow button encouraged visitors to click it and sign a petition, presumably in support of this nationalisation drive. The text of the invitation – written in Ukrainian – was grammatically correct, but was written in a linguistic style that three Ukrainian native speakers told Bellingcat could not have been written by a fluent Ukrainian – including the use of the phrase “Support Mr. President”.
When inspecting the cloned website (between 11-14 February 2022), clicking the button would initiate the download of a zip file containing malware, hidden under the misleading name “PDF – Петиція щодо повернення майна громадянам України” [Petition to return property to the citizens of Ukraine]. The file was not in fact a PDF but had a cpl (control panel) executable extension. A VirusTotal analysis showed that this file contained a host of malware mimicking Trojan behavior.
Possible Goals
It is not clear what the infected file’s functionality would have been once successfully deployed. It is also not known if the intent of the attack actor was to hack into the original domain of the president’s website and substitute it (or redirect it) to the clone – or, in a more modest scenario, to lure visitors directly to the cloned site via links on other websites or emails.
However, the hypothetical deployment of a Trojan to tens or hundreds of thousands of Ukrainians could have been in a position to cause incalculable damage to Ukraine’s internet infrastructure – for instance via co-opting all infected computers into a distributed DDoS attack on a large range of websites – such as the ones targeted today. At the same time it would have exposed files on the infected users’ computers to the attackers – although this would be a less useful outcome given the non-specific group of people targeted via such mass infection methods. A different outcome that Fagerland found to be at least as plausible as the DDoS hypothesis was that such a massive deployment of Trojans might have aimed to steal credentials for social media accounts – possibly with the goal to use them in subsequent online disinformation campaigns.
An additional hypothetical outcome might have been linked to creating political confusion and instability: the bait message – confiscate all oligarchs’ property – chimes with president Zelensky’s own political messaging on the “de-oligarchisation of Ukraine”. But confiscation and redistribution is far more radical than anything Zelensky has espoused publicly; the wide distribution of such a proposal would have likely have caused division and further polarisation in Ukrainian society.
There is no evidence that the infrastructure and malware behind the stun[.]site command-and-control centre was used or linked to today’s cyber attacks experienced by Ukrainian government institutions. However, the unusual form of intended distribution of malware – via a mass-facing clone of a website of the country’s president – shows potential intent to cause large-scale damage to the country’s infrastructure, potentially via a DDoS attack with an unprecedented scale of distribution.
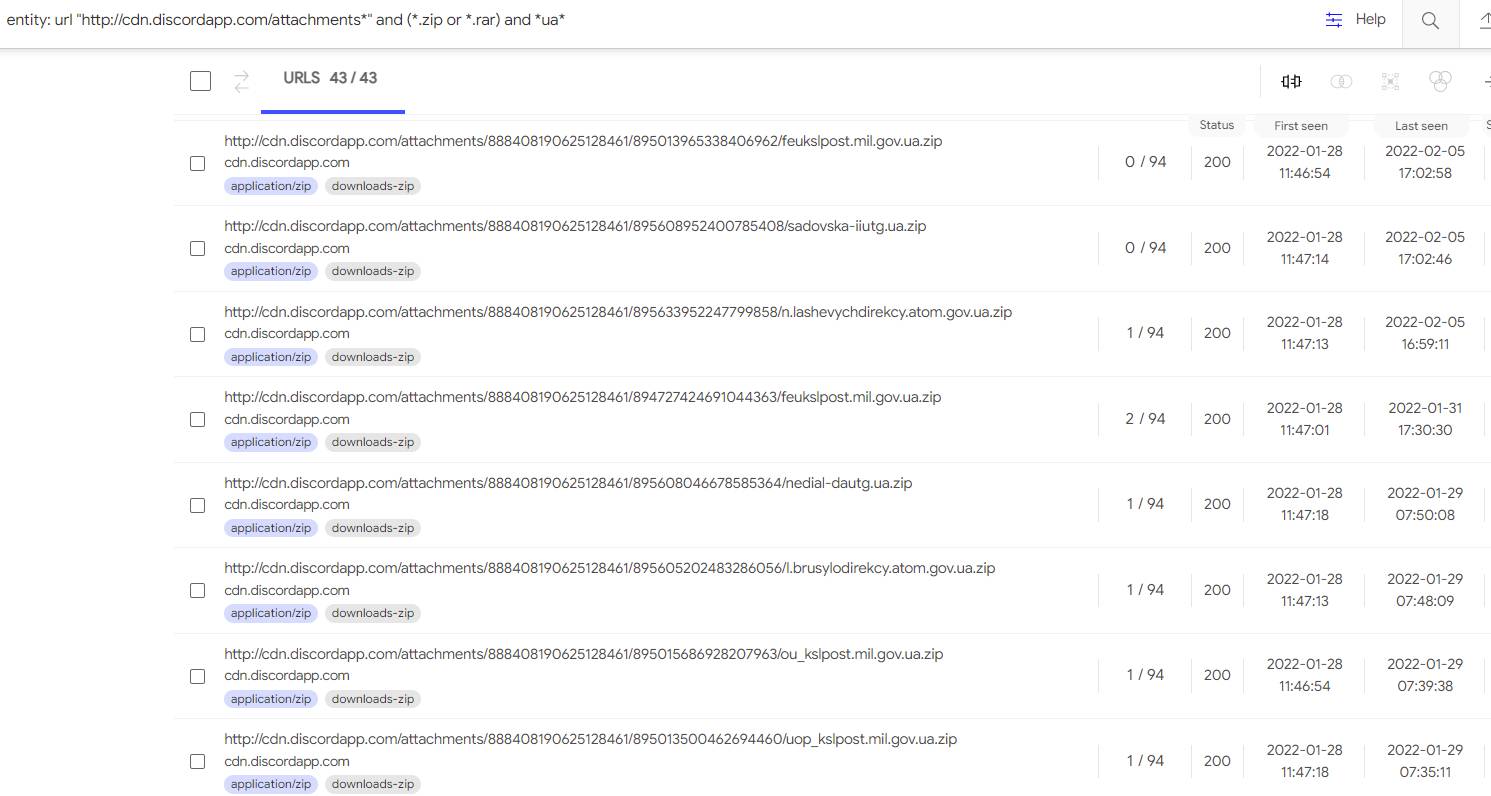
Notably, during the same time frame (January and February 2022), the same threat actors were sending malware in over 35 different zip files via discord links. These packages appeared to be aimed at high-value Ukrainian targets – as evidenced by the file names mimicking domains of Ukraine’s nuclear agency (atom.gov.ua), Ministry of Foreign Affairs (mfa), and its defence ministry (mil.gov.ua).
The malware, once deployed, connected back to 3237[.]site – a domain which had the common registration history and malware load as the stun[.]site. This shows that the threat actors behind the “Support Mr. President” campaign had a sophisticated, diversified and multi-faceted infection and disruption strategy, consistent with the capabilities and needs of a hostile nation-state actor, Fagerland said.
Bellingcat is a non-profit and the ability to carry out our work is dependent on the kind support of individual donors. If you would like to support our work, you can do so here. You can also subscribe to our Patreon channel here. Subscribe to our Newsletter and follow us on Twitter here.