Military And Intelligence Personnel Can Be Tracked With The Untappd Beer App
Surprise! The beer-rating app Untappd can be used to track the location history of military personnel. The social network has over eight million mostly European and North American users, and its features allow researchers to uncover sensitive information about said users at military and intelligence locations around the world.
For people in the military, neither drinking beer nor using social media is newsworthy on its own. But Untappd users log hundreds, often thousands of time-stamped location data points. These locations are neatly sorted in over 900 categories, which can be as diverse and specific as “botanic garden.” “strip club,” “gay bar,” “west-Ukrainian restaurant,” and “airport gate.” As the result of this, the app allows anyone to trace the movements of other users between sensitive locations — as well as their favorite bars, hotels, restaurants, neighbourhoods, and, sometimes, even private residences.
Examples of users that can be tracked this way include a U.S. drone pilot, along with a list of both domestic and overseas military bases he has visited, a naval officer, who checked in at the beach next to Guantanamo’s bay detention center as well as several times at the Pentagon, and a senior intelligence officer with over seven thousand check-ins, domestic and abroad. Senior officials at the U.S. Department of Defense and the U.S. Air Force are included as well.
Cross-referencing these check-ins with other social media makes it easy to find these individuals’ homes. Their profiles and the pictures they post also reveal family, friends, and colleagues.
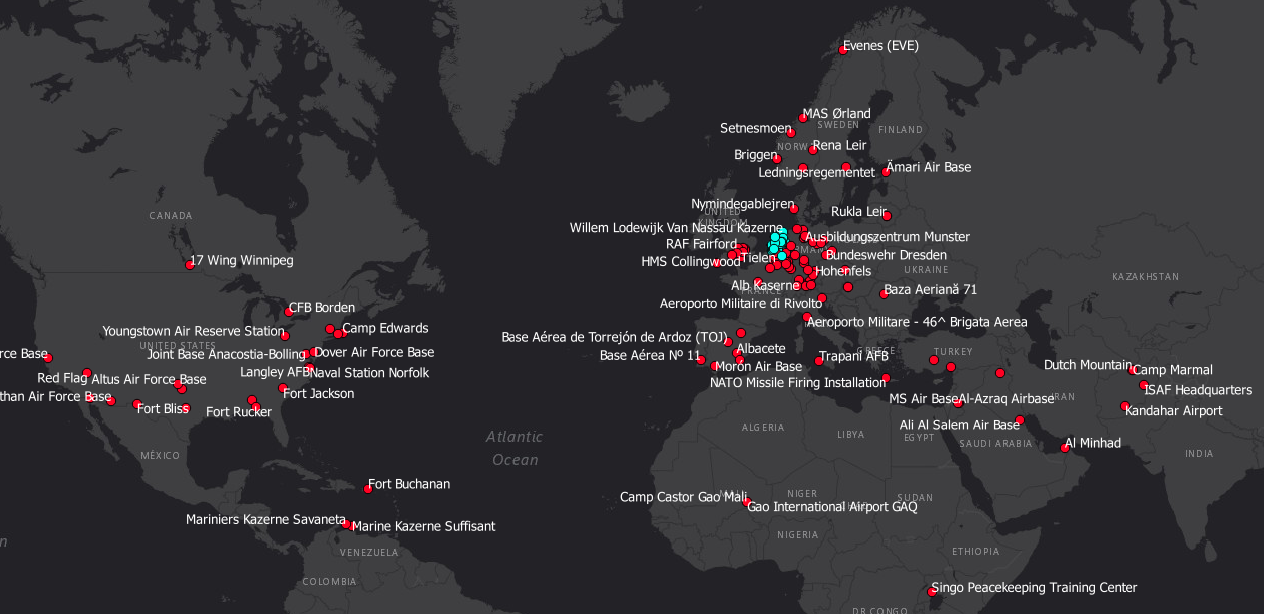
For reasons explained further below, it is difficult to assess the total number of individuals that can be traced this way. Yet sensitive locations such as military bases can easily have hundreds of unique visitors, and beyond Europe, North America, and the Middle East, military users can be found at locations as varied as Greenland, Niger, and South Korea.
The activity level varies per location. Some locations currently have a lot of active users while other locations were briefly used years ago, such as Blackwater / XE’s location in North Carolina. Even the inactive locations can still reveal a lot of data about the visitors and their networks.
Below are examples of a location page and a user’s venue history. On the left is the venue page for Ramstein air base, showing nearly 600 unique visitors that have logged over 2600 beers. On the right, we see a small portion of a single user’s check-in history as he travelled through Afghanistan, revealing his visits to the United States embassy bar in Kabul, the Duck and Cover, among other places. The user also has thousands of other check-ins spread over hundreds of different locations.
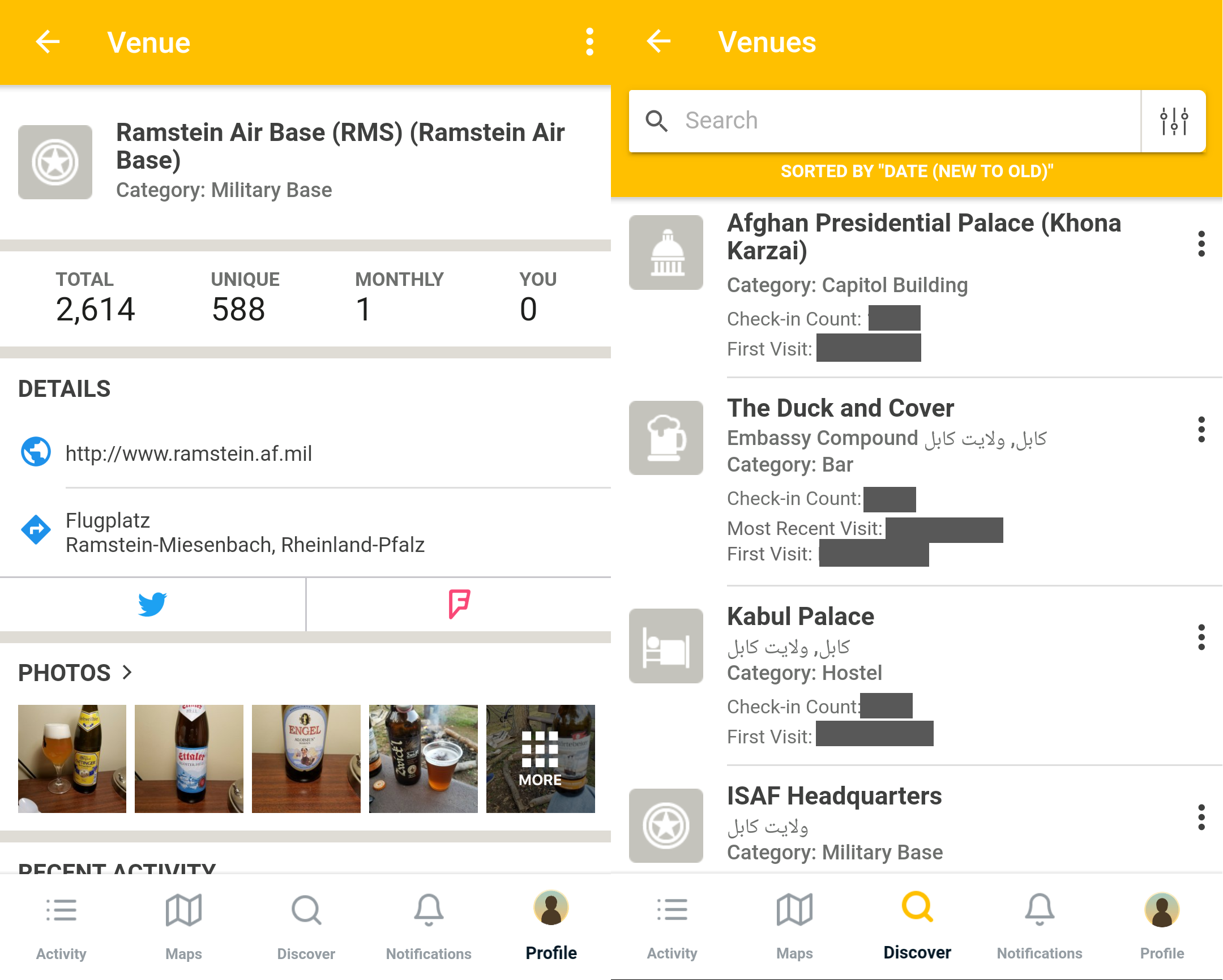
Left: Ramstein Air Base’s venue page within the Untappd app. Right: A part of a user’s check-in history
The only requirement to access this information, i.e. to find individuals working at various military and intelligence organizations and track their general whereabouts, is a little bit of digging in Untappd’s data and cross-referencing it with other social media.
Tapping Untappd
At first glance Untappd’s data might seem useless as its location data is not strict, meaning users are free to check in to locations from up to 60 miles away. This is a problem at well-known spots in more populated areas. For example, the NSA and MI6 headquarters have many check-ins from users who were in the vicinity, but who were likely not inside these buildings.
Moreover, it can be difficult to find locations of interest, as Untappd’s search functions only list venues such as hotels, bars, and restaurants. You cannot search for locations that are tagged primarily as “government building” or “military base,” for example. Complicating matters further is that one location can have multiple pages, and it’s sub-locations can have pages as well, making it difficult to assess how many users are checking in there in total. For example, there are two pages for “The Pentagon,” but also pages for the Pentagon’s courtyard, E-ring, and other areas. These locations are hidden in Untappd’s search functions.
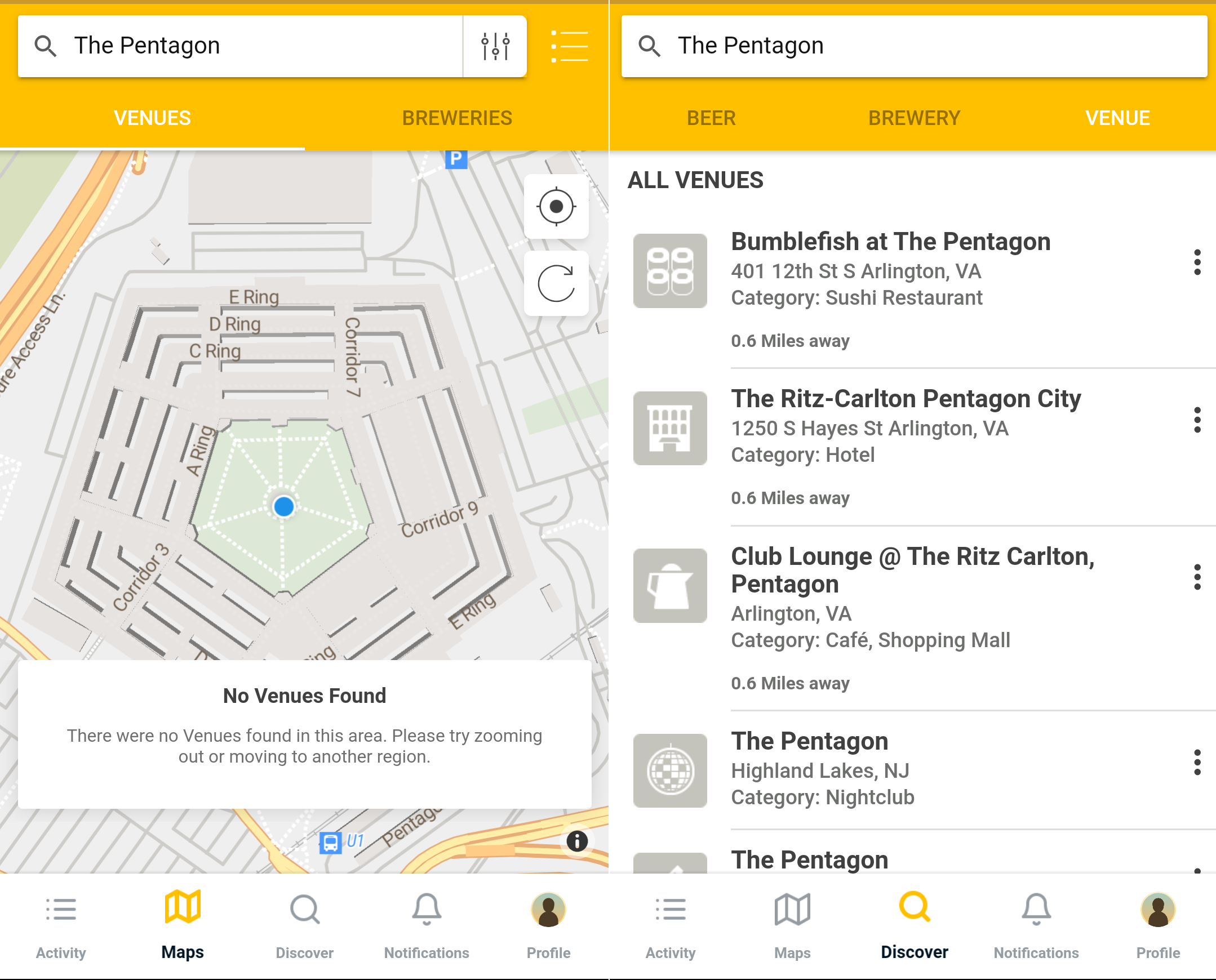
Left: Untappd’s map view when searching for ‘The Pentagon’. Right: Untappd’s search results when searching for ‘The Pentagon’
Given these issues, how can one still manage to find sensitive government locations as well as the individuals who actually visited them?
Here is how this works: When users drink beer, they can “check in” to Untappd by taking a picture of their beverage and logging their location as well as the date and time. Searching for a location brings up only bars, restaurants and shops. Once you begin the process of “checking in” a beer, however, Untappd allows more locations to be selected.
Locations have their own profiles, showing all users who have checked in there, along with the date and time of their check-in. These locations are drawn from Foursquare’s application programming interface (API), and are highly categorized. Searching for military locations does not bring up results. Yet by finding members of the military and piggybacking, you can find other military locations.
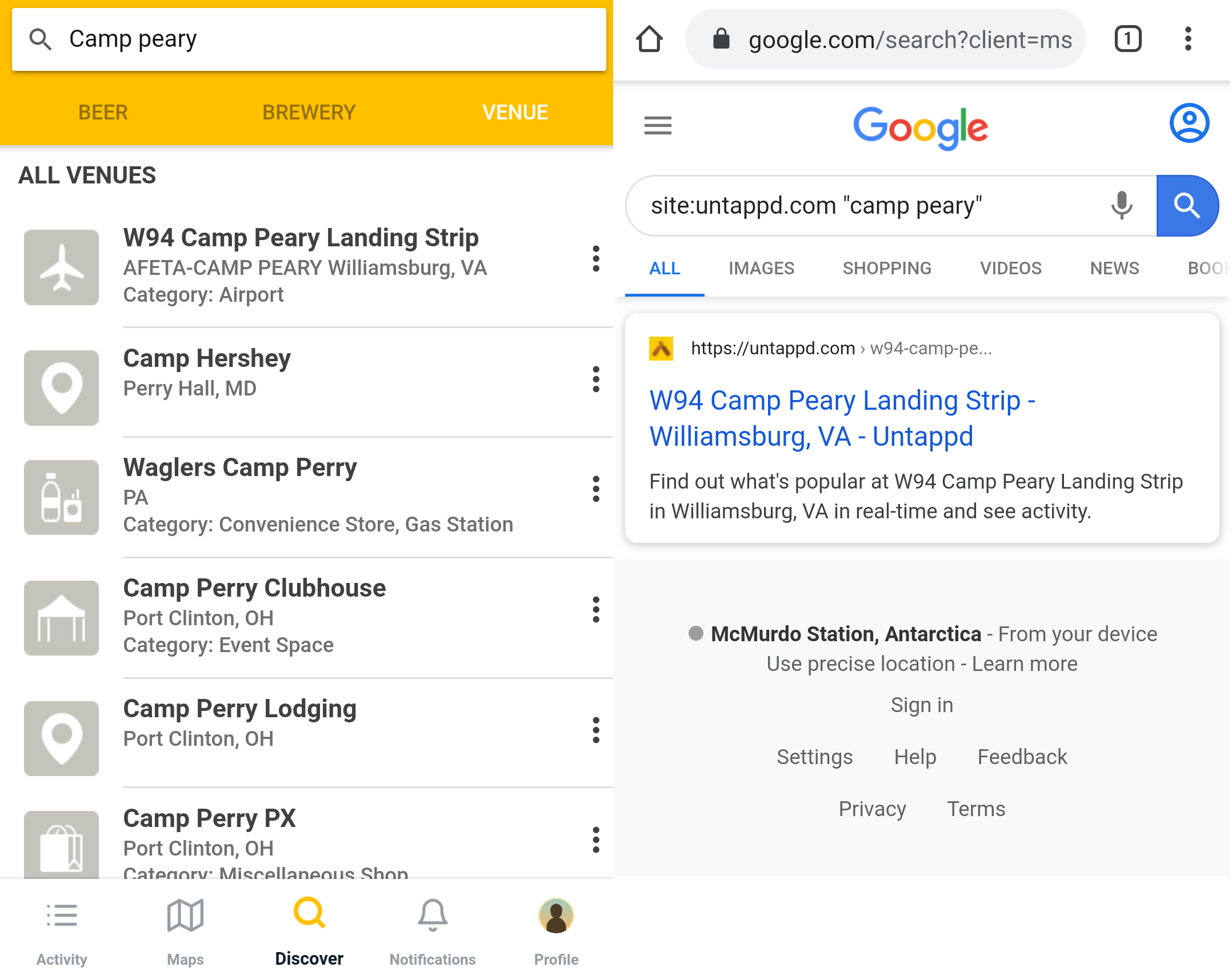
Let’s take Camp Peary, a U.S. military reservation officially referred to as an Armed Forces Experimental Training Activity, though more commonly known as “The Farm.” The location hosts training facilities for personnel from the Central Intelligence Agency (CIA) and the Defense Intelligence Agency (DIA), and has an airstrip which allegedly has been used for rendition flights.
Beginning with a simple search in both Untappd and Google, we can easily find the landing strip at Camp Peary. However, Camp Peary itself does not show up. The probable reason for this is that the landing strip is categorized as an “airport,” not as as “military base.” Looking at the results, we could assume that there simply might not be a registered location for Camp Peary.
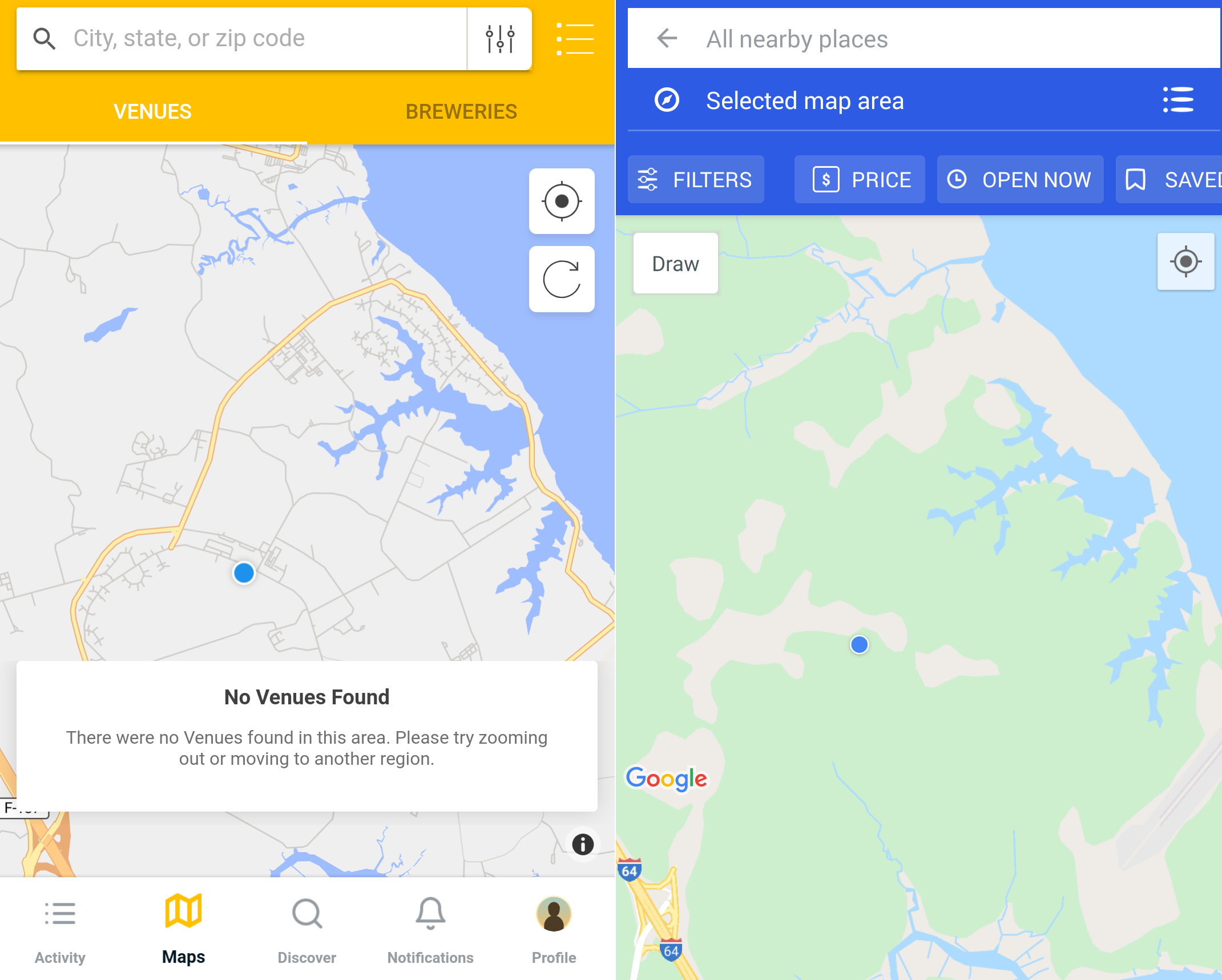
If we navigate to Camp Peary’s location on Foursquare and Untappd, we can verify that neither of the apps registers it as a location.
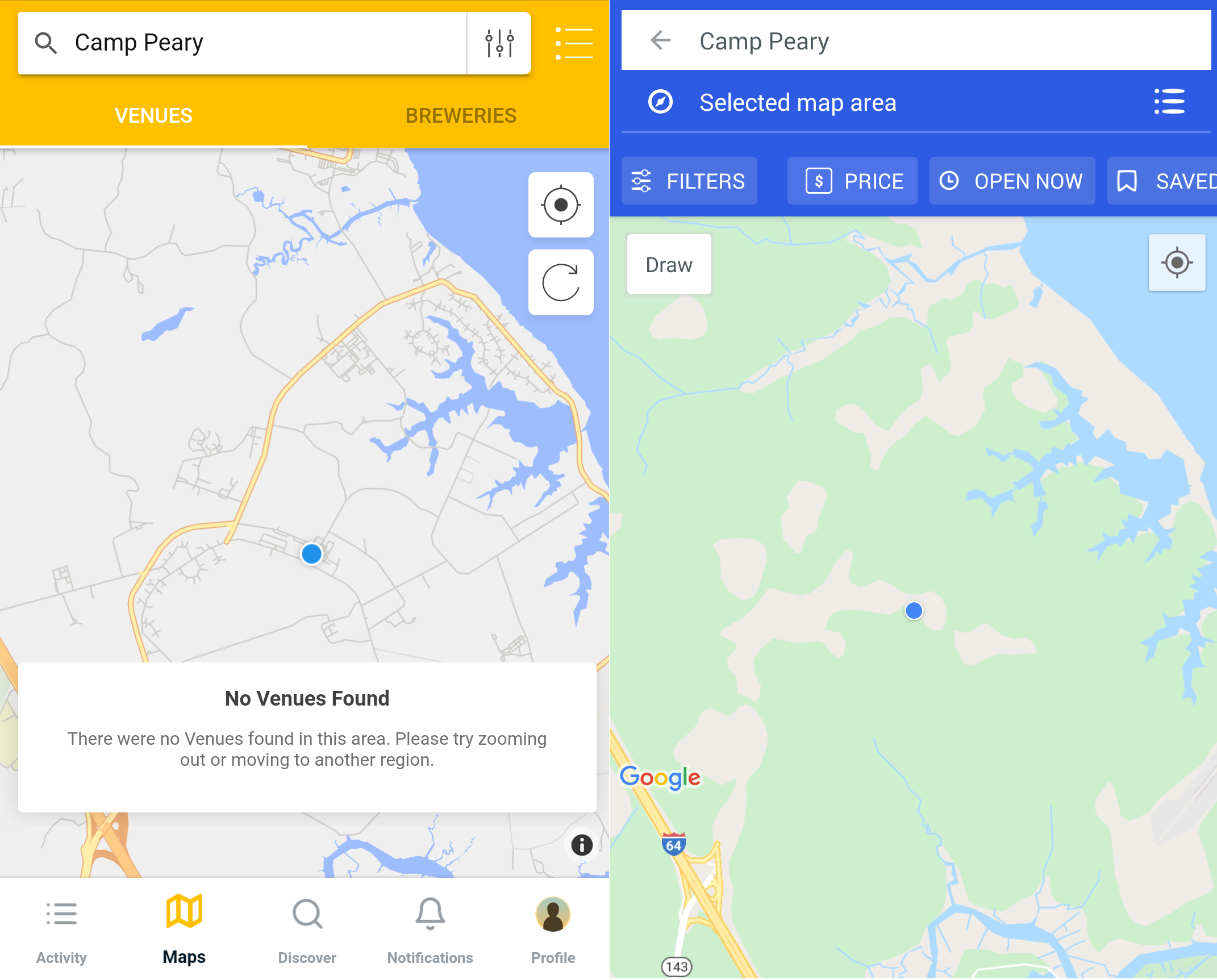
Empty map views at Camp Peary’s location, after searching for ‘Camp Peary’ in Untappd (left) and Foursquare (right)
However, if we search for “Camp Peary” directly in the Foursquare listings, we get the following results:
Notice that Foursquare now gives a result for Camp Peary (though the location does not include useful information). We can also see that the location for Camp Peary is now actually in Foursquare’s map view, which remained blank during our previous searches.
More interestingly, Foursquare reveals Camp Peary while Untappd did not. Remember, Untappd uses Foursquare for all venue information. Untappd appears to actively hide some location categories, including “military base,” from its search results.
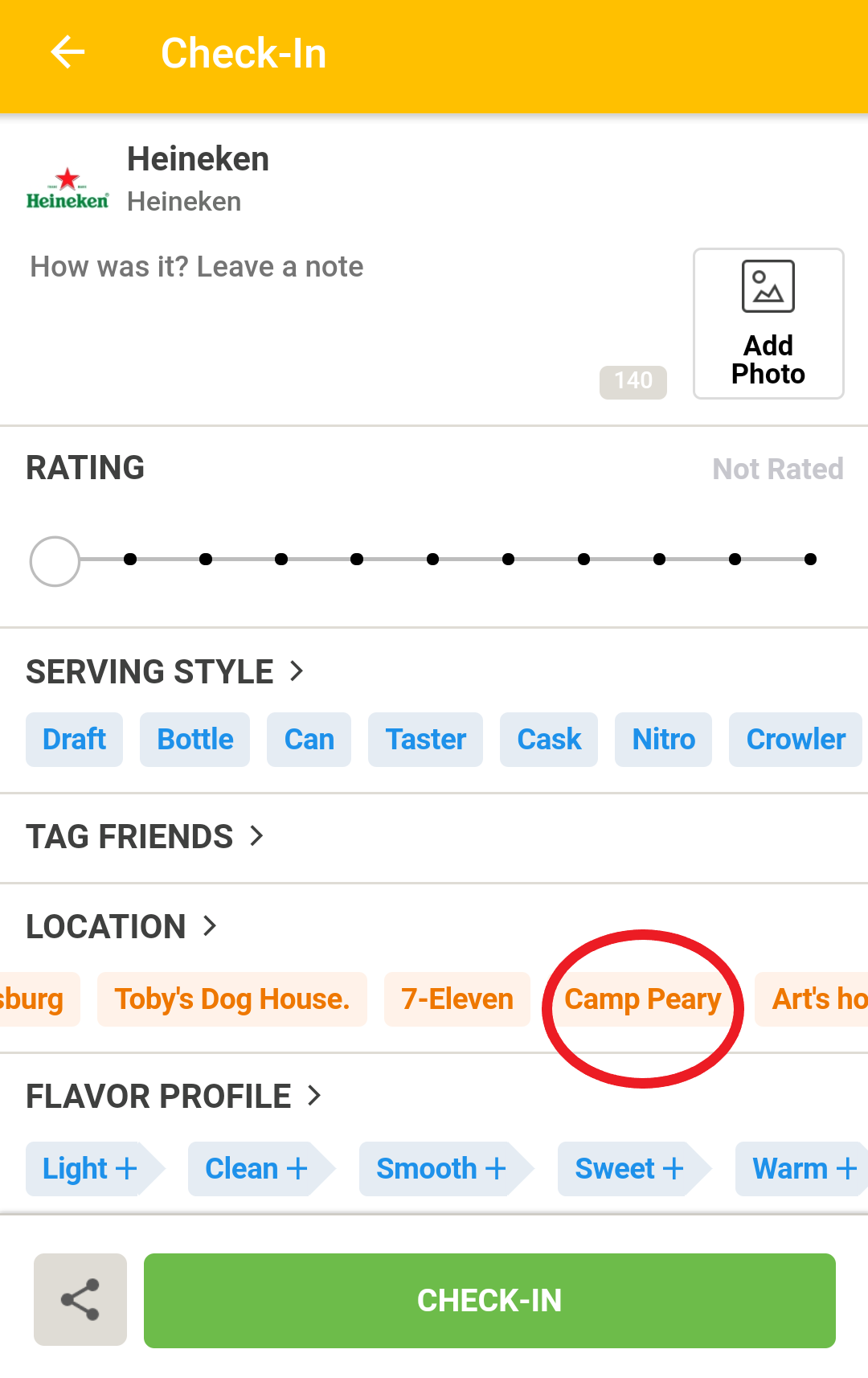
Yet there is one more way Untappd can be searched: by checking in the actual beer. When users log their drink, Untappd can use their device location to suggest other places nearby to check-in. If we spoof our location to Camp Peary’s vicinity and begin the process of checking in a beer, Untappd will reveal that it does know Camp Peary exists.
Make sure your account is set to “private” before the next step. If you do not want to “check in” at all, keep reading for a more privacy-friendly, but cumbersome way to find locations.
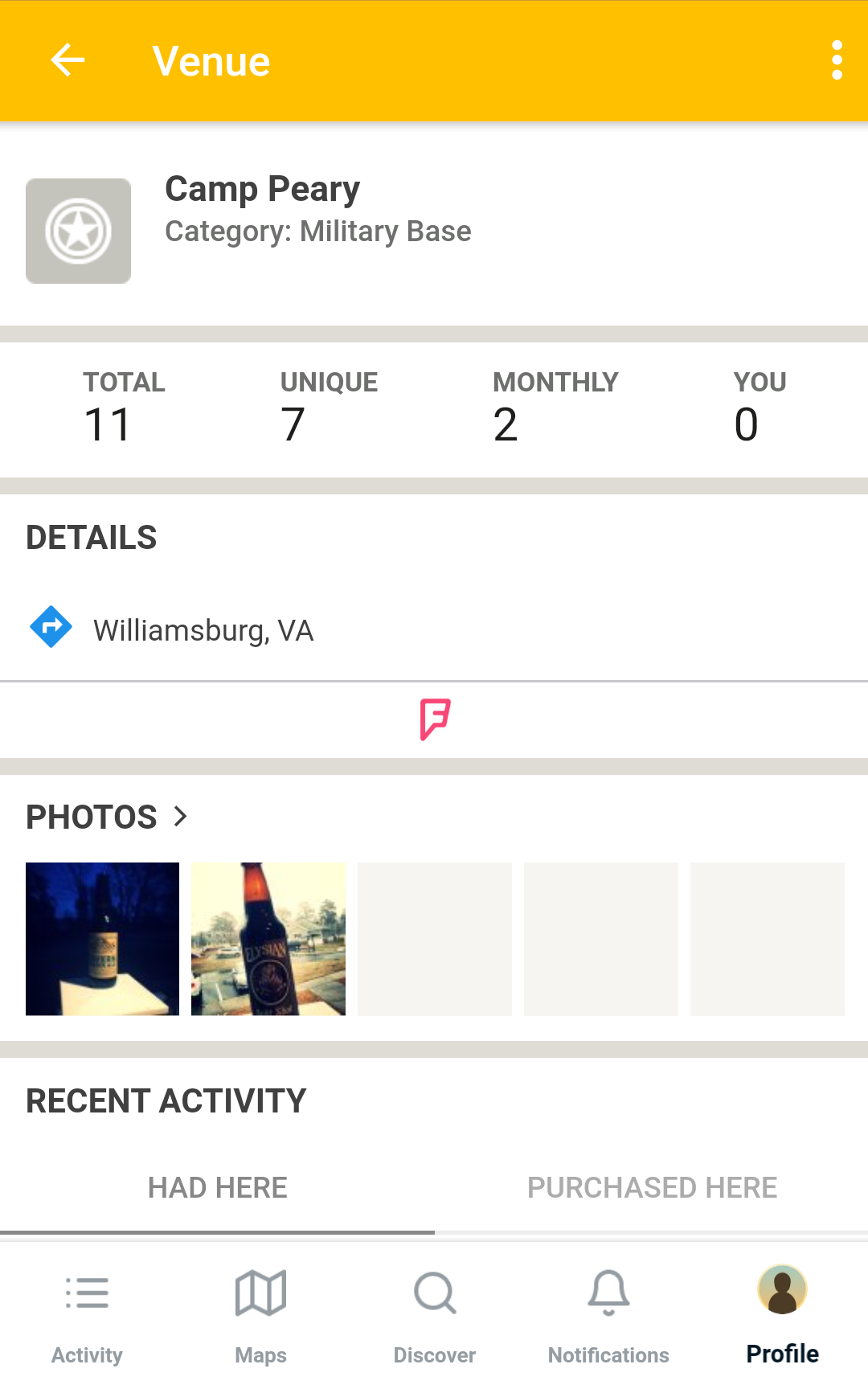
Completing the “check-in” will log the beer on your timeline, along with a link to Camp Peary’s page. On Camp Peary’s page, we can find a timeline of users who have checked-in there, as well as photos associated with the location.
As we can see, several unique profiles have “checked in” at Camp Peary. However, it is possible that these users stumbled upon the Camp Peary location when they were in the vicinity and checked in there for fun, or else that they used our method and spoofed their location on purpose. So how can we check if users were actually there?
Geolocation
The best way to determine whether a user was really in the location to which they checked in is to look at the pictures taken there. Untappd encourages users to upload photos of their beer bottles in order to identify their drinks, and these pictures sometimes include background clues. These background clues allow for geolocation of these images to verify the location of the users who uploaded the pictures.
Continuing to use Camp Peary as our example, we can see pictures have been posted by an individual who has checked in three times. Through geolocation, we can match the features in the picture to satellite imagery of buildings within Camp Peary’s compound. We can also use Untappd’s profile data to confirm the person’s identity by cross-referencing the username and profile picture with other social media.
Location History
Another way to verify the authenticity of check-ins is to browse a user’s profile. A user profile has a timeline, but also a venue list and a list of photos uploaded with each check in. The timeline is limited to the last 365 entries, but the photo list and venue list are unlimited, meaning it is possible to get a full location history.
A user’s venue list is particularly useful, as it can be filtered by category and sorted on frequency and date of visits. Below, you can see the (unverified) history of two users. On the left it is filtered by “government.” and sorted by date of visit. On the right, is sorted by “most frequently,” revealing favorite restaurants, hotels, and private residences (with homes, Foursquare provides the approximate location, rather than the exact one).

Left: A user’s venue history categorized by ‘government’. Right: A user’s venue history sorted by frequency of check-ins
This allows us to get a higher degree of certainty about a user’s check-ins before beginning to verify the user’s photos and cross-referencing with other social media. For example, a user that has visited several military locations across large distances, multiple times, over a longer period of time, is more likely to be associated with that location than a user who has only checked in there once.
For example, the user who checked in at Camp Peary has also checked in at military locations throughout the Middle East, and has logged an additional 700+ check-ins at 500+ unique locations. A similar check of the user near the Guantanamo Bay detention center shows that he paid several visits to the Pentagon, as well as other military installations. Again, through their check-in history and cross-referencing with other open sources, we can identify the user in question.
The other locations these users have checked in paint a very rich picture of where they live, how they travel, and which places they frequent. Most of their check-ins are accompanied by a photo of their drinks, sometimes revealing family, friends, and colleagues in the background.
Scaling Up
Through the location history of a user identified at a military location, it becomes possible to discover other military locations. Each new military location might reveal other users, and those users might in turn reveal new military locations.
In other words, we can now piggyback on users we have identified by looking at their location histories, instead of having to spoof our location and check in. Keep in mind that this approach also has its limitations, as users can be confined to a certain set of locations depending on the branch they work in.
If you visit Untappd venue locations through the web rather than the app, they will list “loyal patrons,” the top 15 users that have checked in most frequently at that location. These are perfect candidates to piggyback on, as they are both likely to have a strong connection to that location, and be active users that will be checking in elsewhere as well. This allows us to map connections between locations.
For example, by examining users that are “loyal patrons” of Dutch military locations (light blue) and identifying the other military locations (red) they have visited, we can begin to map out possible Dutch military connections across the globe, including locations of military exercises and missions:
By comparing the location history of several different users, it also becomes possible to identify non-military locations that they have in common. Think, for example, about bars and restaurants near sensitive locations that their visitors might go to in their spare time. In the Dutch example, it is possible to identify a resort soldiers went to after a mission, in order to transition from military to civilian life.
Social Drinkers
Apart from the expansive location history, Untappd also works as any other social media network. Users can post messages accompanying their check-ins, tag friends, get likes, and add each other to friends lists. Upon registering, users are asked to provide a username and full name. Though Untappd only shows the first letter of the last name to other users, the combination with the username can help reveal the full name. For example, John Doe’s profile might show “John D. (Jdoe2002)”. On top of that, users can also connect Twitter and Facebook to their profiles.
As with any social media, the photos can reveal more information on their own too. The difference is that with Untappd, the photo’s tend to focus a bit more on tables or desks where users place the bottle, and that they might be taken by slightly inebriated users a bit more often. They include desktops, documents and plane tickets, but they also feature military hardware from time to time. Below are pictures taken at military installations.

Pictures of documents on military matters, clearly not meant for public consumption, posted on Untappd
Why Publish These Findings?
In our previous investigation of a fitness app revealing the homes of military and intelligence personnel, we did not publish the findings until the company behind the app rendered the data inaccessible and made changes to its privacy standards. This is not the case with Untappd.
Untappd differs in three crucial ways: It has decent privacy settings, as profiles can be set to “private” easily. Users have to consciously select locations they check in to. Most importantly, private residences are not registered unless a user has added their own home. In other words, with Untappd, the onus is on the user for the data they share.
At the same time, Untappd’s data can be a useful source of potential leads for investigations, or as a point of reference to confirm other findings. This article has focused on the military, but businesses and political locations can be found there as well. It is a stark reminder that Untappd and smaller social networks like it, though they tend to draw less attention, are worth checking when conducting open source investigations — and can also present serious security challenges.
Users discussed in this article have been notified and have adjusted their privacy settings accordingly. Made possible in part by Fontys Academy of Journalism.