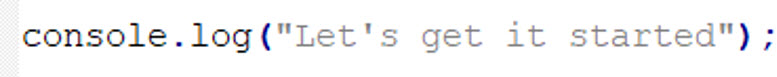Guccifer Rising? Months-Long Phishing Campaign on ProtonMail Targets Dozens of Russia-Focused Journalists and NGOs
A sophisticated phishing campaign targeting Bellingcat and other Russia-focused journalists has been much larger in scope than previously thought, and has lasted at least several months. Bellingcat has identified dozens of targeted individuals across Europe and the US, with the earliest reported attack dating back to April 24 2019, and some evidence suggesting the campaign was in the works since as early as March 2018.
The target list of over 30 individuals using the end-to-end encrypted ProtonMail email service includes journalists, researchers, academics, employees of NGOs, and political activists. The one common denominator among them is the Russian focus of their research or activist work. Contrary to previous reporting, we have identified that at least some of the phishing attempts have been successful.
Bellingcat believes that this phishing campaign formed a stage of a larger ongoing hacking operation against Russia-focused journalists and researchers, with various methods and tools – some of them without precedent – being deployed against a range of targets both within Russia and abroad.
“A Most Sophisticated Phishing Campaign”
The active, publicly traceable phase of the phishing operation began in early April, when the perpetrators registered 11 domains intended to impersonate ProtonMail mail-hosting sites. Bellingcat has identified five different domains that were used between April 26 and July 23 2019 when our initial reporting led to a closure of the offending websites. These domains were:
my[.]secure-protonmail[.]com (April and May)
actions[.]protonmail[.]team (May)
mail[.]protonmail[.]systems (June and July)
mail[.]protonmail[.]sh (July)
mailprotonmail[.]ch (July)
Based on an iterative technique termed “timestamp pivoting” , cyber-threat consultancy ThreatConnect were able to identify a further 6 domains registered by the same actor group. Timestamp-pivoting essentially scouts out domains that were registered in close temporal proximity to the known offending domains, on the assumption that cyber-crime actors purchase groups of a domains in single transactions to minimize resources and exposure.
mailprotonmail[.]com
protonmail[.]direct
protonmail[.]gmbh
prtn[.]app
protonmail[.]support
prtn[.]xyz
Timestamp-pivoting is not a bullet-proof algorithm and is most likely to be successful with domains registered via smaller registrars. That said, ThreatConnect’s approach did identify two domains that we later confirmed to have been used for the phishing operation. We have not identified phishing traffic from any of the remaining registered domains.
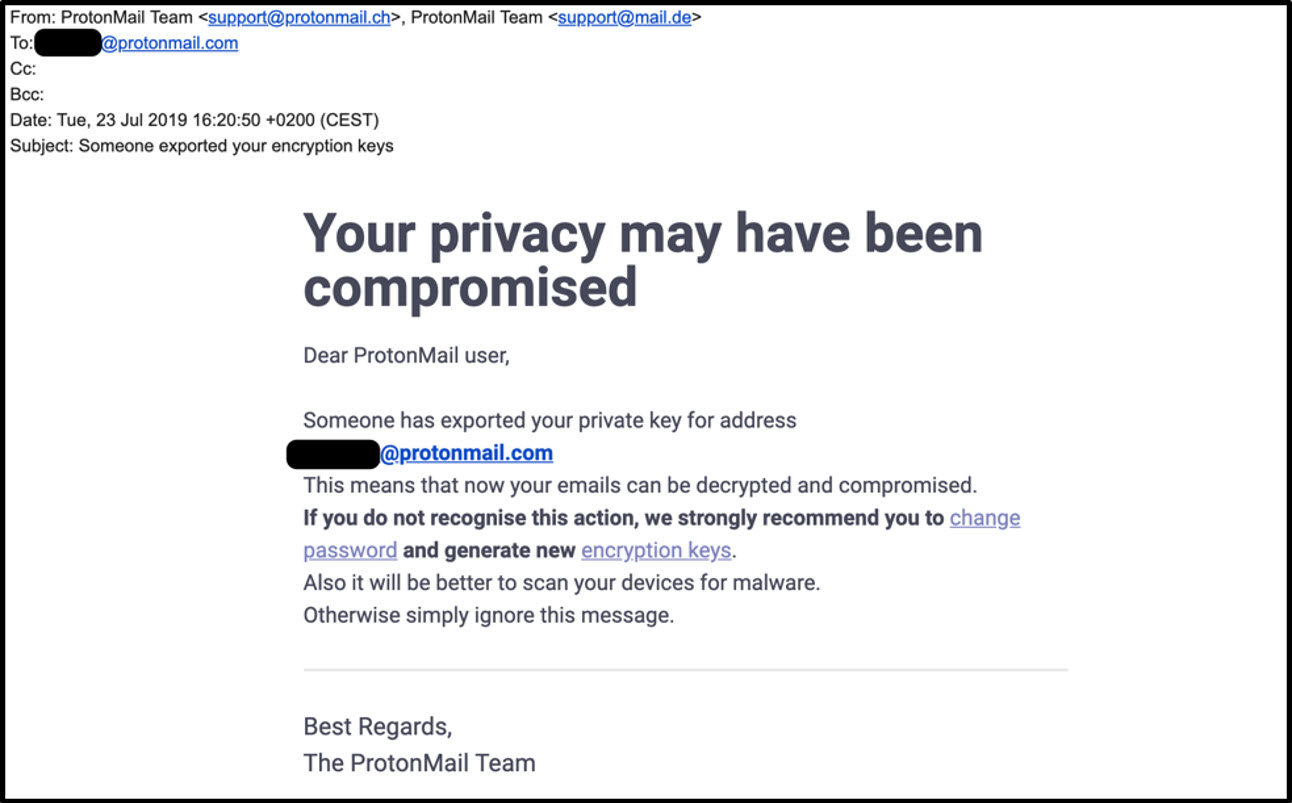
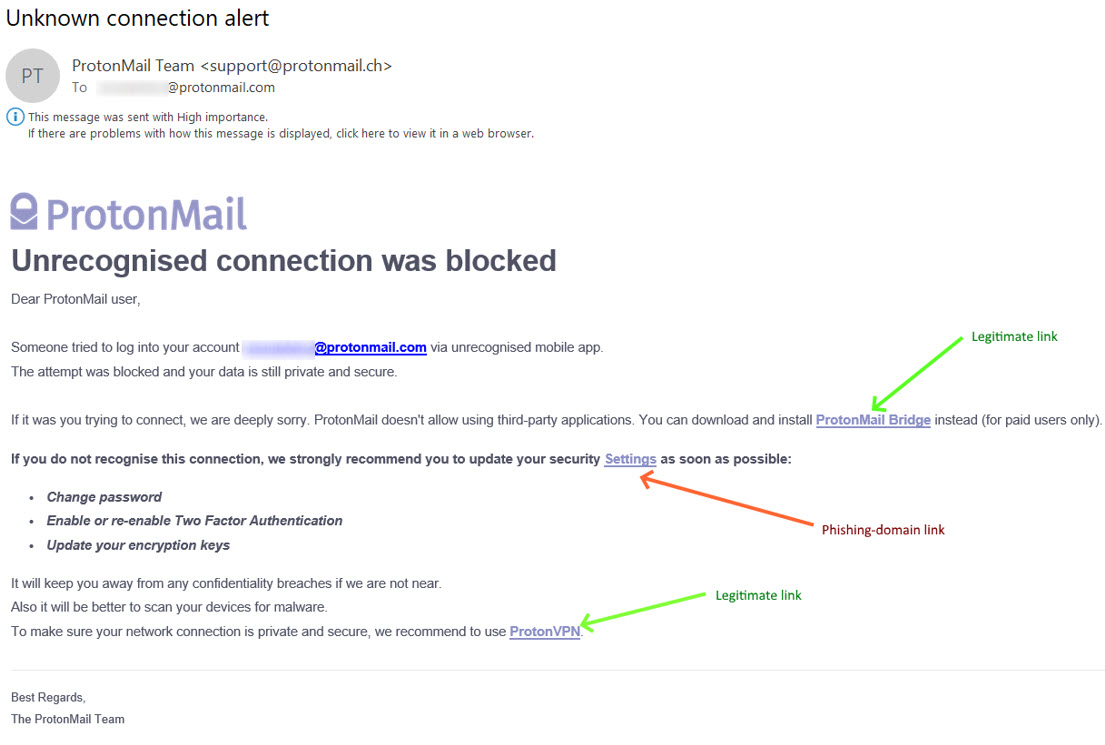
The phishing messages were in fact fake ProtonMail alerts suggesting the user’s email account had been compromised or subject to suspicious login attempts. The messages came in 8 different flavors, with one of the following subject lines: “Unrecognised connection was blocked”, “Unknown connection alert”, “Someone knows your Protonmail password”, “ProtonMail unusual network activity”,” ProtonMail suspicious login”, “Keep your ProtonMail account secure”, “New login from unusual place”, and “Someone exported your encryption keys”.
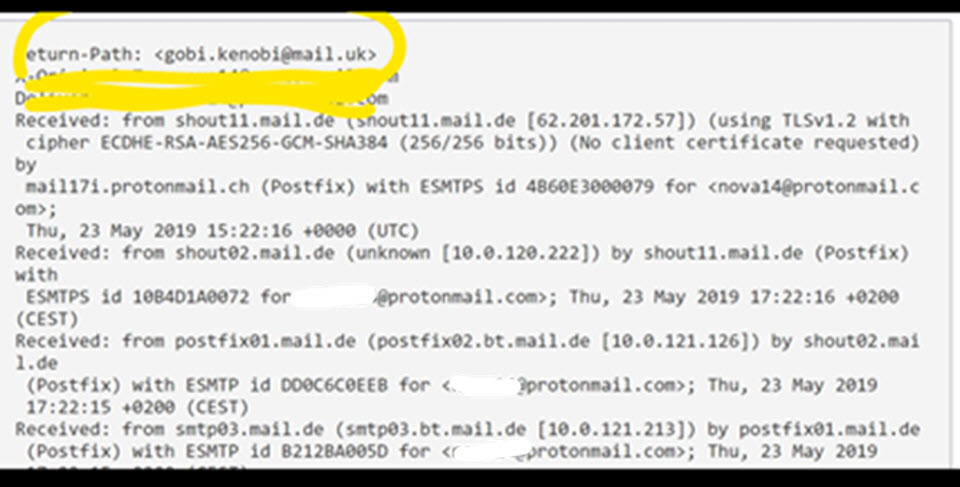
The sender optically appeared usually as support[@]protonmail.ch (a legitimate Protonmail service account). However, email headers show that this sender address was spoofed, with the actual sender – visible in the Return-Path variable – being one of three external web-mail accounts hosted at the Germany-based free mail service mail.uk: kobi.genobi[@]mail[.]uk, notifysendingservice[@]mail[.]uk and xavi.alonso[@]mail[.]co[.]uk. We identified that the first two of these accounts have been closed by Mail.de after the initial publications about phishing campaign; however the third one is not closed as of press time. (Our detailed list of questions about the incident and the closure of the two accounts to the owner of the mail service, Mail.de GmbH, were not answered.)
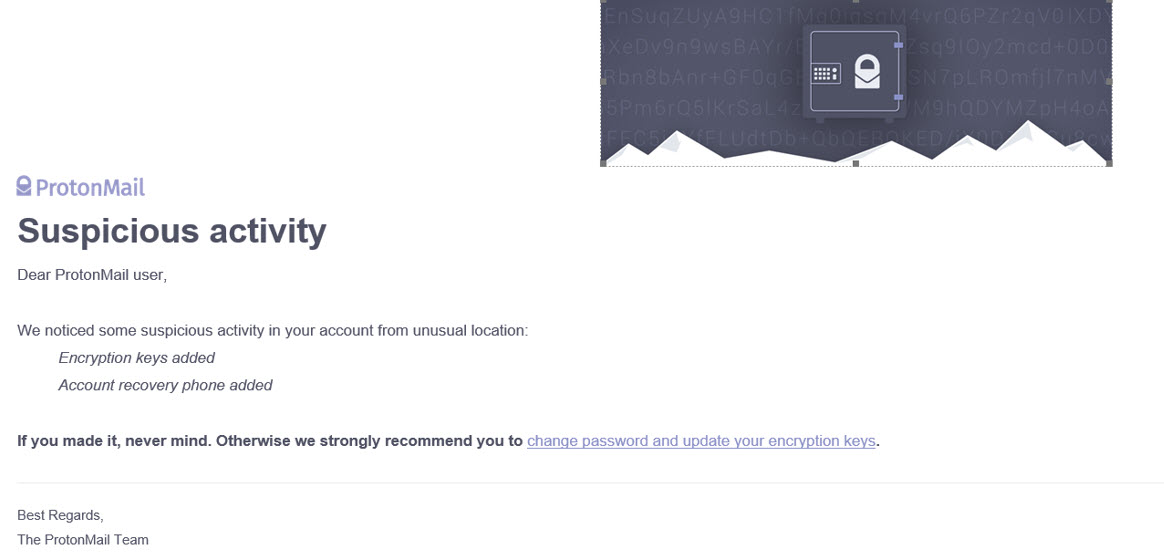
However, we have identified at least one case – in the earliest stage of the phishing campaign in April – which used Protonmail’s own internal mail server, and thus used full end-to-end encryption of the communication between phishing party and the target. The email from which this phishing attempt came was notifier-no-reply[@]protonmail.com. It is not clear why the perpetrators switched to an external mailing service for their subsequent attempts. A possible explanation might have been a concern that ProtonMail might identify and blacklist such sender addresses more easily, and/or would have more forensic evidence in the form of detailed access logs in case of an investigation.
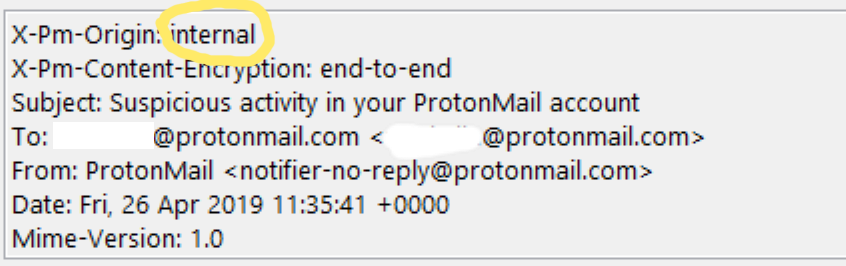
Example of a phishing email that arrived from “within” the ecosystem of Protonmail. In this case the full message chain – including the content of the phishing message – was end-to-end encrypted.
The body of the phishing emails included different variations of security alerts about exported private keys or suspicious log-in attempts. The design of the messages followed closely ProtonMail’s own house-style, and while there were minor linguistic inconsistencies, they convincingly emulated security alert messages. In each case the message contained hyperlinks to “Settings”, “Keys” or “Password” sub-paths on a look-alike external domain, encouraging the user to click through and “secure” their account. In some cases in the later stage of the campaign, the phishing hyperlinks were interspersed with valid, decoy links to the real ProtonMail domain intended to reassure the victim that they are dealing with a legitimate email.
What exactly happened once a victim clicked through is not conclusively established yet, and is the subject of ongoing investigations by at least two leading cybersecurity firms, and by ProtonMail itself. While the initial assumption was that the operation had tried to steal log-in credentials, the volume and complexity of the Javascript code used by the phishing sites has raised the possibility that there may have been additional nefarious activity proactively performed by the script without the user’s knowledge or interaction. At press time, Bellingcat had provided reconstructed copies of the malicious code to ThreatConnect, CrowdStrike and ProtonMail, and the three companies are still reviewing its functionalities.
ProtonMail, whose CEO described this phishing operation as “the most sophisticated [he has] ever encountered”, was earlier quoted as saying that the fake login scripts of the fake domains were “synchronized with the real ProtonMail login process for simultaneous login, to trick users into also giving up their two-factor authentication codes”.
Post-mortem of a Successful Phishing Attempt
We have investigated the browser cache logs and ProtonMail login authentication logs of one targeted user whose account appears to have been briefly compromised. The user received the following carefully crafted phishing message that included decoys in the form of two legitimate links to the authentic ProtonMail domain, and one “payload” link to the fake domain.
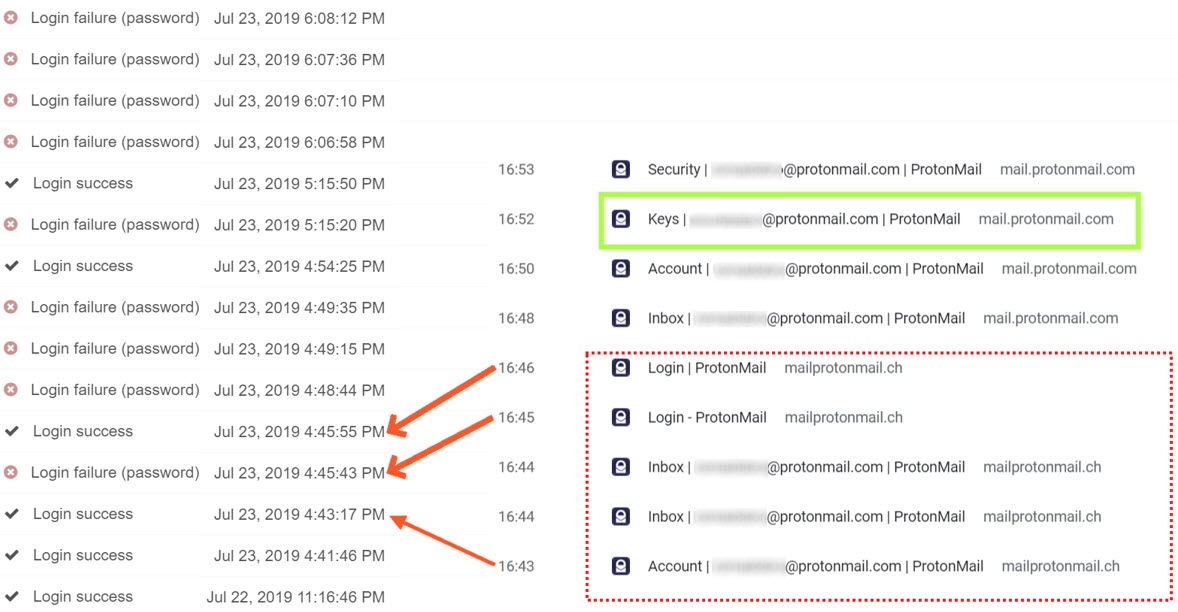
A contemporaneous view of two logs: on the left, the authentication (log-in) log of ProtonMail, on the right, the sites and subpaths visited by the user’s browser at the same time.
- At 15:58 the user received the phishing mail seen above, but did not notice it until (see login success at 16:41:46 above,) when he logged in to his account using the legitimate ProtonMail log-in portal
- At 16:43 the user read the phishing email and clicked on the “Settings” link which took them to an “Account” sub-path of the fake mailprotonmail[.]ch domain.
- At 16:44 the user clicks on the Inbox tab of the fake domain, trying to return to his emails screen. This triggers the Log-in portal of the fake website, which is apparently where the credential harvesting takes place.
- There are two log-in attempts at 16:45, both made at the fake-site log-in portal. The first one results in a wrong-password refusal by ProtonMail, and the second one succeeds. It is not clear if this was the result of the user mistyping the password the first time, or of a sophisticated synchronized login algorithm which may require two consecutive login attempts, the first one with a randomly generated false password fed by the fake server to the real one while the real password is being stolen, and the second one submitting the harvested password to the ProtonMail server. (Notably, we reviewed the browser cache of another user – who was also briefly compromised – and the same double-visit to the login portal is visible, suggesting this is intended behavior by the phishing actor.)
- Following the successful credential harvesting, the user’s browser is redirected to their legitimate ProtonMail inbox (16:48 event).
- In this particular case, the targeted user reportedly realized something was wrong and – making sure they were in the authentic Protonmail portal – went to their account settings and changed their password (at 16:50) and private keys (at 16:52), and introduced 2FA (at 16:53). This led to them successfully logging in again with the new credentials at 16:54:25.
- At 17:15 there was a sequence of a log-in failure and log-in success which cannot be matched to browser activity, which is likely the result of the user logging in via their mobile application.
- Beginning at 18:06, there is a sequence of failed log-in attempts which are not followed by a successful log-in. ProtonMail told us they believe that these failed attempts were made by the phishing actor, who was trying to access the mail account using the (outdated) credentials previously stolen.
It is not clear what the phishing actors were capable of harvesting during the several minutes during which they had valid credentials for the target’s account. At the very minimum, it appears that they were able to harvest the contact list in his mailbox, as discussed below. Whether or not they were able to download contents of email messages is uncertain; the failed log-in attempts approximately 20 minutes after the credentials were stolen suggests there may not have been an automatic download functionality embedded at the phishing server. Neither ThreatConnect nor CrowdStrike were willing to put forward hypotheses about the likely functionality of the phishing script without further research into the voluminous JS code used by the actor.
The Targets List
Bellingcat was first made aware of phishing attempts via ProtonMail on 2 July 2019, when a European private investigation firm with a focus on Russia informed us that three of its employees had received phishing messages containing the “Your private keys have been exported” bait. This attack had occurred in the last days of June 2019. The targets’ accounts had not been breached, however the fact that their non-public and non-eponymous account names had become known to a phishing actor implied that another person who corresponded with them via ProtonMail might have been previously breached.
On 23 July 2019, Bellingcat researcher Christo Grozev and two journalists, one based in Russia (Roman Dobrokhotov) and one in the UK (Mark Burnett), who had recently collaborated on a joint investigation of Russian military intelligence activities, discovered phishing emails with different message bodies in their ProtonMail accounts. At this point, Christo Grozev appealed via Twitter to others who may have been targeted to contact him, with the goal of creating an inventory of the type of targets sought by the phishing actor. As of today, we have identified at least two dozen accounts that have been targeted by this phishing campaign. It is beyond doubt that these people have been targeted by the same actor(s) due to the overlap in use of infrastructure in the form of domain names and sending SMTP servers (see ThreatConnect’s analysis of the infrastructure used). All targets are involved in work focused on Russia, and most have previously been subject to public attacks – either personally or institutionally – by the Russian government.
These accounts may be grouped in the following categories:
- Journalists: including Bellingcat researchers (2), BBC investigative journalist (1), Guardian journalists (3), and journalists from different Russian investigative media (3). At least two of the targeted foreign journalists are known to have previously banned from traveling to Russia.
- NGO’s with a focus on Russia or assisting Russian independent media (10 targets). Several of these organizations asked to not be named publicly, in order to discourage further attacks. The list of NGOs included, for instance, the Prague-based European Values Think Tank which has been vocally critical of Russian disinformation efforts in Central Europe, and the Free Russia Foundation.
- Investigators and academics focused on Kremlin’s foreign policy and Russian clandestine operations abroad (6)
Account name Harvesting
Given that ProtonMail users tend tо emphasize the privacy of their communication, most of them select email account names that are not easily matched to their real names, and do not publicize their ProtonMail identities. This raises the question as to how the phishing actors were able to amass the target list accounts, given that according to information from ProtonMail, there was no guess work (I.e. no brute-forcing) involved, and the perpetrators knew exactly the accounts they were after.
Iterative harvesting
Our analysis shows that at least in certain of the cases, the phishing actor used an iterative approach where, after successfully penetrating the mailbox of a “patient zero” (whose account name they knew one way or another), they were able to identify accounts of interest from among the victim’s contact list, and then proceeded iteratively in a tree-like fashion with further victims. By following the chain of phishing attempts starting from this “patient zero”, we were able to establish that the harvested contacts lists were not “mass-mailed” by the phishing actor; instead only persons of interests were picked and targeted with phishing emails.
- On 26 April 2019, the ProtonMail account of a London-based user working at an NGO that provides funding to Russian independent media and human rights activists was successfully compromised for approximately 5 minutes before the account owner changed their password. We have no information as to how this user’s email was initially acquired, but given that this phishing date was not long after the registration of the first domain used in the attacks, it is possible that this was a “patient zero” for this particular branch – i.e. that the perpetrators had acquired their ProtonMail account via a different route (such as humint or a non-ProtonMail hack).
- Following the successful hack, some (but not all) of this “patient zero”s ProtonMail contacts received phishing emails. They were not sent immediately following the hack, and were not all sent at the same time.
- Nearly 3 months later, at 13:38 CET on 23 July 2019, one of these contacts (Target 1), an investigative journalist, received a phishing email. This person’s account was also compromised at 14:41 for approximately 2 minutes before it was secured again (see description above).
- Approximately 40 minutes later , at 15:20 CET, one of Target 1’s contacts – Target 2, a journalist based in a different country – received a differently worded phishing email. As he was already alerted, he did not click through.
- At some point later the same day, a third journalist (Target 3, in a third country) who was a contact of Target 2 but not of Target 1, received a phishing mail. Crucially for this investigation, Target 3 had no other ProtonMail contacts than Target 2. However, Target 2 had previously forwarded an email from Target 3 to Target 1 (as all three were collaborating on a Russia-focused investigation). This would have made the ProtonMail username of Target 3 visible to the phishing actor who had briefly compromised Target 1’s account. Target 3 was duly warned and did not click through to the phishing links.
The above case study shows the likely iterative method the phishers used to discover target accounts of interest. This is particularly clear in the case with Target 3 who had no other ProtonMail contacts than Target 2 who had only shared Target 1’s email with one other person – who was compromised.
Group harvesting
In another phishing case identified by us, several ProtonMail users with non-eponymous accounts received phishing emails at approximately the same time. These accounts – which belonged to various categories of users including NGO representatives, journalists and academics – were linked to only one joint activity: attending a one-day seminar focused on overseas activities of Russian intelligence. This invitations-only seminar was not publicly announced and was coordinated via secure messaging, however an attendees contact list – including in certain cases ProtonMail accounts – was compiled by the organizers. It is plausible that this address list became the initial harvest list for this group phishing wave. We do not have information on how this address list may have been procured by the phishing actor.
Tracing the Perpetrator
Attribution of a modern phishing campaign is not a straight-forward and rarely a deterministic process, especially if the actor is sophisticated and well-funded. Availability of anonymized VPN and Tor-based access, throw-away email accounts and SIM-cards, and bitcoin payments means that the whole infrastructure chain needed to perpetrate a large-scale attack can be procured and paid for untraceably. Thus, absent occasional human blunders, attribution is possible largely on the basis of circumstantial evidence.
The profile of the phishing targets is one way to come up with a short-list of potential actors. In this case, all (known) targets were professionally engaged with activity that is deemed hostile by the Russian government – from investigations of GRU’s covert operations to Russia’s alleged meddling in UK and US political processes. This narrows down the candidates to either the Russian state (the default hypothesis), or a false-flag attack by an adversary of Russia trying to discredit it. (A third possible hypothesis is that this was the work of a para-state Russian actor, i.e. a Russian entrepreneur “investing” in such activity nominally on their own behalf. Because such “private” actors have been previously shown to act on behalf of – and with beneficiary funding from – the Russian state, we will not distinguish this hypothesis from the default one).
It is notable that several of the targets of this campaign (both within the Bellingcat team and among Russian journalists) have been targeted in phishing campaigns dating back to 2015 and 2016 that have been attributed to Fancy Bear, the cyber-army of Russia’s military intelligence GRU whose hackers were indicted over their hack of the DNC. Those previous attacks were highly sophisticated, in some cases using as bait custom-written fake documents that were ostensibly “leaked” to journalists.

Screenshot of fake Ukrainian parliamentary bill, custom-drafted as bait for a phishing campaign in September 2015
The overlap in targets between previous and the current phishing operations plus the resources and time needed to build up the n competence and infrastructure necessary for such as a sophisticated operation makes Fancy Bear a likely candidate for the recent operation. Circumstantially this is also corroborated by the use of Njalla and Web4Africa resellers to procure domain infrastructure – these providers have been previously used by Fancy Bear, although obviously this is not an exclusive relationship.
A State Actor
Our preliminary analysis of the source code used on the phishing sites implies that the campaign was the work of a state actor and not of an individual hacker or a hacker collective.
One indirect reason for attribution to a state actor is the time that it required to build (or re-purpose) the code and infrastructure for the operation. Bellingcat was able to reconstruct (a large part) of the malicious code by harvesting the browser cache of a targeted computer. We found that the main background image used on the log-in portal of the fake site was an edited version of the ProtonMail image and contained Metadata that the original does not. The modifications to the image on the fake site were made on 8 March 2018. This suggests that the ProtonMail phishing campaign has been in the planning stage for over a year.
Another intriguing detail to the campaign is that there seems to have been at least one “development” website associated with the same operation and used for several months prior to its operational launch. This site was discovered by Marcus Neis, Threat Intel Manager at Swisscom, who found an overlapping SHA256 fingerprint between this site and one of the phishing websites.
Nice work, also always good to keep in mind that adversaries reuse their tooling. Searching for same response content by sha256 e.g. on @censysio brings back another host with still active @ProtonMail phishing https://t.co/HCV2LkiztF – possibly related but unconfirmed https://t.co/H80NrmWZg4 pic.twitter.com/xb9IboEmC1
— markus neis (@markus_neis) July 28, 2019
This website existed without an associated domain name, reachable only via its IP address, hosted at a shared cloud/VPS server run by China’s Alibaba.Net. The site represented a spoofed version of the ProtonMail log-in portal. It could be linked to the operational (spoofed) website not only by the identical SHA256 fingerprint but also by the use of the background graphics with the same metadata. The code on the website was different from both the original ProtonMail and the operational malicious phishing websites, and contained some elements of both. However the core functionality file – vendors_index_chunk.js, was very similar to that on the functional phishing website(s), and had nothing in common with the legitimate ProtonMail code. This suggests the China-hosted web server was either a “development” server used by the perpetrators for testing purposes, or alternatively a template that was developed by a third party and made available to phishing actors. However, the identical SHA256 fingerprints makes this latter hypothesis less likely. This “precursor” website was taken offline on 6 August 2019, almost two weeks after the phishing campaign was first exposed.
A review of the Javascript source code on the operational website shows the hallmarks of a professionalized, structured coding operation. It is clear that sizeable effort had been invested in reverse-engineering ProtonMail’s own architecture. Much of the original code is retro-commented, memorializing the reverse-engineer’s understanding of the functionality of certain pieces of code (such comments would be typical of a diligent original coder, however are missing from ProtinMail’s own source code).
Once again, such diligence in reverse-engineering would imply a structured environment with multiple coders that need a shared understanding of the code, and would be atypical for a hacker or a hacker collective.
While most of the used code that emulates ProtonMail’s functionality is different from the original Javascript used by the Swiss company, it is largely a professionally rehashed collection of preexisting open-source modules available on code-sharing repositories such as Github.com.
Linguistic clues
Many of the comments interspersed in the tens of thousands lines of code used by the phishing site (which combines newly written code, adjustments to existing code and whole segments of borrowed open-source code) indicate that the coder or coders were not native English speakers. Grammatical tense mismatch and wrong word order are particularly prevalent. However, this in itself may not be used as an indication of country of provenance of the coders, as many coders have a functional grasp of English but are not necessarily grammatically proficient.
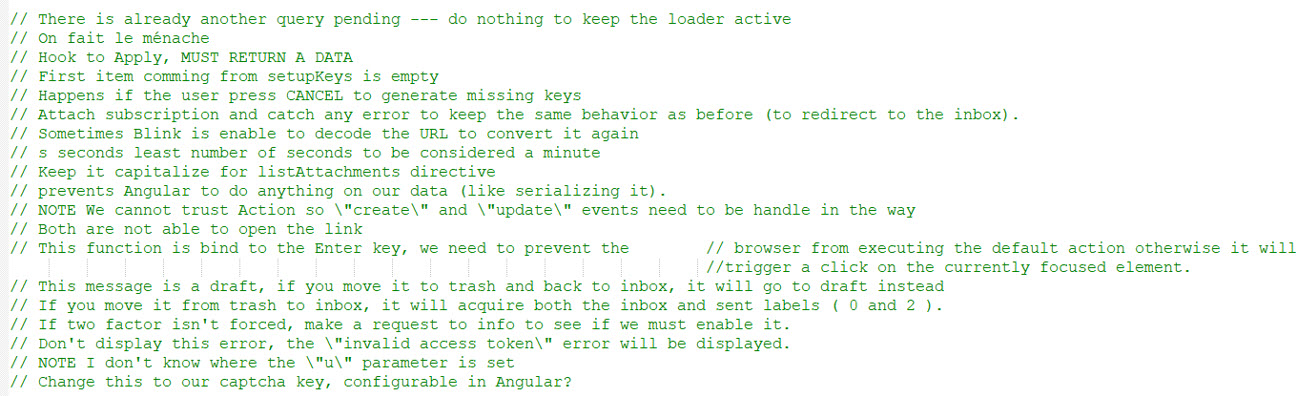
A collection of comments interspersed among the code on chunk.0.js, a dynamically compiled javascript file
One console log message inserted by the phishing script coders, however, maybe be of particular interest as a linguistic clue. This message is inserted in 0.chunk.js Javascript file partly “borrowed” from the original Protonmail. Just before the first modification in the code by the phishing actor(s), the following message is logged to the browser’s console:
This piece of code has no functional relevance other than to mark the start of action of the amended, malicious code. The choice of phrase appears somewhat unusual, as the more common English wording would have been “Let’s get started”. Possibly coincidentally, this version of the phrase appeared in the FAQ section of the WordPress website of fake online persona “Guccifer 2.0” – a cover for the Fancy Bear hacking team, pursuant to US indictment documents.

Screenshot from the “coming out” post on the now-defunct WordPress website run by the online persona “Guccifer 2.0”
Bellingcat is making the core Javascript files used by the phishing site available for analysis here.
Ongoing hacking attempts
After the disclosure of the phishing operation following Bellingcat’s appeal for victims to come forward, this particular operation was quickly discontinued, partly due to actions by law enforcement authorities and by ProtonMail itself. However, recent developments suggest that some of the targeted journalists and researchers may be subject to ongoing hacking attempts – plausibly by the same actor due to the time proximity to the now incapacitated phishing campaign. One disconcerting example is the combination of offline and online hacking operation against Roman Dobrokhotov, also targeted in the phishing campaign. Late in the day on 8 August 2019 he discovered that his mobile telephone can no longer connect to the network. After checking in with the support desk of his mobile provider, Russia’s market leading cell operator MTS, he was told that he had received a replacement SIM card earlier in the day. In order for a person to obtain a replacement SIM card – which by default deactivates the currently used SIM card – a person must appear at an MTS service center and show their passport to prove ownership of the number. Obviously, someone had impersonated Roman Dobrokhotov with a passport in his name – or had otherwise breached the MTS protocol for issuance of a new SIM card (MTS are currently investigating the issue).
Notably, the first thing that the number-hijacker did, was to log in to Dobrokhotov’s social media (VKontakte) account, to which goal they had to change the associated email and used the telephone number to prove their association with the account. As no fake-posting and no other activity such as defacing the account was observed, clearly the hacker sought to acquire information held in the private messages in the Vkontakte account.
Other targets of the phishing campaign have also reported suspicious activity on their non-ProtonMail accounts, and in one case on a privately owned server. Bellingcat will continue investigating and report on these cases.
The Official Investigation
Both ThreatConnect and ProtonMail confirmed to us that their own investigations point to a likely Russian origin of the phishing attack, however both deferred to law enforcement agencies as the only authorities that would be able to access raw technical data – such as IP access logs for hosting providers, third-party email provider access logs, etc – that might enable hard attribution.
As of press time, Bellingcat is aware of an ongoing investigation into the phishing operation by Swiss law enforcement. Dutch and French authorities – where IP addresses used for the different stages of the operation were located – were also informed by several targeted users of possible criminal activity on their respective territories, and may have initiated their own investigations.